Don't Copy From This Blog...
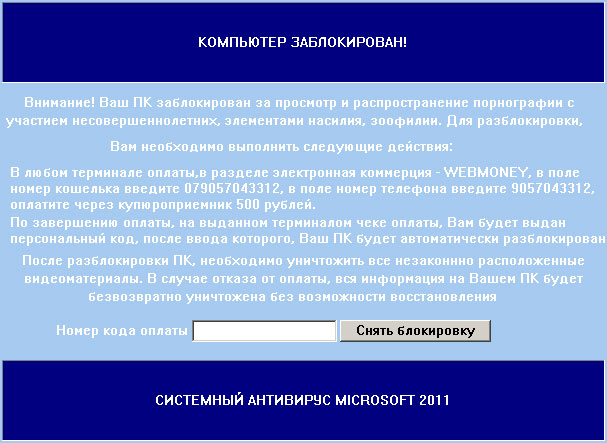
СИСТЕМНЫЙ АНТИВИРУС MICROSOFT 2011 (System Antivirus Microsoft 2011) is a Russian ransomware that prevents you from accessing your files and programs until you pay a fee via SMS text message (500 рублей ~ $17). A code key is require to unlock the computer and regain access. It claims that your computer was blocked because you were watching/downloading illegal videos. СИСТЕМНЫЙ АНТИВИРУС MICROSOFT 2011 malware further states that your files will be deleted if you won't pay the ransom. This category of malware is usually distributed through the use of fake porn websites. You know, the type of websites where you need to install flash player in order to view videos, although, you already have the latest flash player installed on your computer. In this case, cyber crooks targets mostly Russian internet users, however, you may get infected as well, especially if you're looking for some crazy Russian porn, etc. You should visit only safe porn websites. Also, make sure your anti-virus software is updated. Anyway, if your computer is infected with the СИСТЕМНЫЙ АНТИВИРУС MICROSOFT 2011, you can either enter the unlock code or remove it manually. The unlock code is probably not going to happen because they change it very often and besides, those phone numbers work only in Russia. You will have to reboot your computer in Safe Mode with Command Prompt, restore Windows Shell values and remove the malicious executable file. To remove this ransomware, please follow the steps in the removal guide below. Good luck and be safe online!КОМПЬЮТЕР ЗАБЛОКИРОВАН!
Внимание! Ваш ПК заблокирован за просмотр и распространение порнографии с
участием несовершеннолетних, элементами насилия, зоофилии. Для разблокировки,
Вам необходимо выполнить следующие действия:
В любом терминале оплаты,в разделе электронная коммерция - WEBMONEY, в поле
номер кошелька введите [], в поле номер телефона введите [],
оплатите через купюроприемник 500 рублей.
По завершению оплаты, на выданном терминалом чеке оплаты, Вам будет выдан
персональный код, после ввода которого, Ваш ПК будет автоматически разблокирован.
После разблокировки ПК, необходимо уничтожить все незаконнно расположенные
видеоматериалы. В случае отказа от оплаты, вся информация на Вашем ПК будет
безвозвратно уничтожена без возможности восстановления
СИСТЕМНЫЙ АНТИВИРУС MICROSOFT 2011
СИСТЕМНЫЙ АНТИВИРУС MICROSOFT 2011 malware removal instructions:
1. Reboot your computer is "Safe Mode with Command Prompt". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Command Prompt" and press Enter key. Login as the same user you were previously logged in with in the normal Windows mode. Read more detailed instructions here: http://www.computerhope.com/issues/chsafe.htm

2. When Windows loads, the Windows command prompt will show up as show in the image below. At the command prompt, type explorer, and press Enter. Windows Explorer opens. Do not close it.

3. Then open the Registry editor using the same Windows command prompt. Type regedit and press Enter. The Registry Editor opens.

4. Locate the following registry entries:
HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\
In the righthand pane select the registry key named Shell. Right click on this registry key and choose Delete.

HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\
In the righthand pane select the registry key named Shell. Right click on this registry key and choose Modify.

Default value is Explorer.exe.

Modified value data points to Trojan Ransomware executable file.

Please copy the location of the executable file it points to into Notepad or otherwise note it and then change value data to Explorer.exe. Click OK to save your changes and exit the Registry editor.
5. Remove the malicous file. Use the file location you saved into Notepad or otherwise noted in step in previous step. In our case, "СИСТЕМНЫЙ АНТИВИРУС MICROSOFT 2011" was run from the My Documents. There was a file called porn_video.exe.
Full path: C:\Documents and Settings\Michael\My Documents\porn_video.exe

Go back into "Normal Mode". To restart your computer, at the command prompt, type shutdown /r /t 0 and press Enter.

6. Download free anti-malware software from the list below and run a full system scan.
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe, explorer.exe or winlogon.exe. With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
7. If the problem persists, please follow the general Trojan.Ransomware removal guide.
Associated СИСТЕМНЫЙ АНТИВИРУС MICROSOFT 2011 ransomware files and registry values:
Files:
- [SET OF RANDOM CHARACTERS].exe
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\ "Shell" = "[SET OF RANDOM CHARACTERS].exe"
- HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\ Shell" = "[SET OF RANDOM CHARACTERS].exe"

















0 comments:
Post a Comment