Don't Copy From This Blog...
AntiVirus AntiSpyware 2011 is rogue anti-virus software that displays fake messages saying that your computer is infected by viruses, spyware and other types of malware. It utilizes false scan results, browser hijackings and other misleading methods in order to scare you into purchasing the program. It may report up to 300 infections on your computer during virus scan. Such type of misleading software provides the user with no protection whatsoever. In other words, it pretends to be a legitimate antivirus program but instead of actually protecting your computer against malicious software and Internet threats, AntiVirus AntiSpyware 2011 provides a false sense of security. This application is a complete scam. If you've got a computer infected by this rogue anti-virus program, you should follow the steps in the AntiVirus AntiSpyware 2011 removal guide below.

AntiVirus AntiSpyware 2011 is from the same family as AntiVirus System 2011.
AntiVirus AntiSpyware 2011 blocks virtually everything you try and run, including legitimate anti-malware tools. It displays fake and very annoying security alerts saying that your computer is infected with spyware, adware and worms that can steal your sensitive information and delete important files. That's not true. What is more, AntiVirus AntiSpyware 2011 displays a fake Windows Security Center and states that hackers are trying to steal your computer license key. That's complete nonsense too.

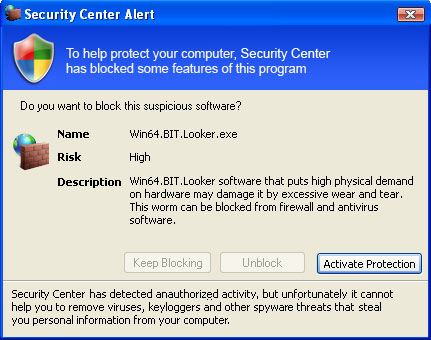
So what happens when you click the "Active" button? You actually get redirected to a fraudulent payment processing site where you can purchase the software. AntiVirus AntiSpyware 2011 related websites:

AntiVirus AntiSpyware 2011 hijacks Internet Explorer and redirects you to either a fraudulent payment processing site or completely unrelated and malicious websites. This rogue application cannot be removed through add/remove programs. If you have already purchased this rogue program, please contact your credit card company and state that the program is a scam and that you would like to dispute the charge. To remove AntiVirus AntiSpyware 2011, please follow the steps in the guide below. If you have additional information regarding this computer infection, please leave a comment below. And if you've got any further questions about this malware, please don't hesitate to contact us. Good luck and be safe online!
AntiVirus AntiSpyware 2011 removal instructions (in Safe Mode with Networking):
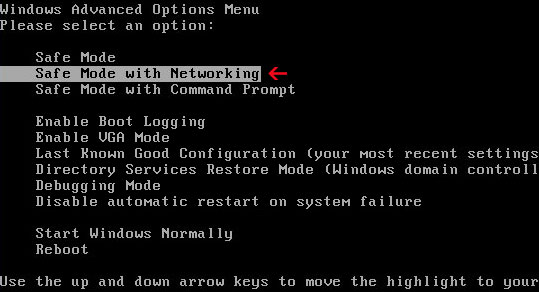
1. Reboot your computer is "Safe Mode with Networking". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key. Read more detailed instructions here: http://www.computerhope.com/issues/chsafe.htm
NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. Download free anti-malware software from the list below and run a full system scan.
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe, explorer.exe or winlogon.exe. With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
3. New threats appear every day. In order to protect your PC from such (new) infections we strongly recommend you to use ESET Smart Security.
Alternate AntiVirus AntiSpyware 2011 removal instructions using HijackThis or Process Explorer (in Normal mode):
1. Download iexplore.exe (NOTE: iexplore.exe file is renamed HijackThis tool from TrendMicro).
Launch the iexplore.exe and click "Do a system scan only" button.
If you can't open iexplore.exe file then download explorer.scr and run it.
2. Search for such entry in the scan results:
O4 - HKCU\..\Run: [Security Manager] C:\Documents and Settings\[User Name]\Application Data\AntiVirus AntiSpyware 2011\securitymanager.exe
O4 - HKCU\..\Run: [AntiVirus System 2011] "C:\Documents and Settings\[User Name]\Application Data\AntiVirus AntiSpyware 2011\AntiVirus_System_2011.exe" /STARTUP
O4 - HKCU\..\Run: [2hdpwq51skqnz] C:\Documents and Settings\[User Name]\Desktop\AntiVirus_AntiSpyware_2011\AntiVirus AntiSpyware 2011\securityhelper.exe
Select all similar entries and click once on the "Fix checked" button. Close HijackThis tool.
OR you can download Process Explorer and end AntiVirus AntiSpyware 2011 processes:
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe, explorer.exe or winlogon.exe. With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
4. New threats appear every day. In order to protect your PC from such (new) infections we strongly recommend you to use ESET Smart Security.
Associated AntiVirus AntiSpyware 2011 files and registry values:
Files:
In Windows XP:

AntiVirus AntiSpyware 2011 is from the same family as AntiVirus System 2011.
AntiVirus AntiSpyware 2011 blocks virtually everything you try and run, including legitimate anti-malware tools. It displays fake and very annoying security alerts saying that your computer is infected with spyware, adware and worms that can steal your sensitive information and delete important files. That's not true. What is more, AntiVirus AntiSpyware 2011 displays a fake Windows Security Center and states that hackers are trying to steal your computer license key. That's complete nonsense too.


So what happens when you click the "Active" button? You actually get redirected to a fraudulent payment processing site where you can purchase the software. AntiVirus AntiSpyware 2011 related websites:
- antivirusantispyware2011.com
- antivirusantispyware2011ltd.com
- antivirusantispyware2011comp.com
- antivirusantispyware2011corp.com

AntiVirus AntiSpyware 2011 hijacks Internet Explorer and redirects you to either a fraudulent payment processing site or completely unrelated and malicious websites. This rogue application cannot be removed through add/remove programs. If you have already purchased this rogue program, please contact your credit card company and state that the program is a scam and that you would like to dispute the charge. To remove AntiVirus AntiSpyware 2011, please follow the steps in the guide below. If you have additional information regarding this computer infection, please leave a comment below. And if you've got any further questions about this malware, please don't hesitate to contact us. Good luck and be safe online!
AntiVirus AntiSpyware 2011 removal instructions (in Safe Mode with Networking):
1. Reboot your computer is "Safe Mode with Networking". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key. Read more detailed instructions here: http://www.computerhope.com/issues/chsafe.htm

NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. Download free anti-malware software from the list below and run a full system scan.
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe, explorer.exe or winlogon.exe. With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
3. New threats appear every day. In order to protect your PC from such (new) infections we strongly recommend you to use ESET Smart Security.
Alternate AntiVirus AntiSpyware 2011 removal instructions using HijackThis or Process Explorer (in Normal mode):
1. Download iexplore.exe (NOTE: iexplore.exe file is renamed HijackThis tool from TrendMicro).
Launch the iexplore.exe and click "Do a system scan only" button.
If you can't open iexplore.exe file then download explorer.scr and run it.
2. Search for such entry in the scan results:
O4 - HKCU\..\Run: [Security Manager] C:\Documents and Settings\[User Name]\Application Data\AntiVirus AntiSpyware 2011\securitymanager.exe
O4 - HKCU\..\Run: [AntiVirus System 2011] "C:\Documents and Settings\[User Name]\Application Data\AntiVirus AntiSpyware 2011\AntiVirus_System_2011.exe" /STARTUP
O4 - HKCU\..\Run: [2hdpwq51skqnz] C:\Documents and Settings\[User Name]\Desktop\AntiVirus_AntiSpyware_2011\AntiVirus AntiSpyware 2011\securityhelper.exe
Select all similar entries and click once on the "Fix checked" button. Close HijackThis tool.
OR you can download Process Explorer and end AntiVirus AntiSpyware 2011 processes:
- AntiVirus_AntiSpyware_2011.exe
- securitymanager.exe
- securityhelper.exe
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe, explorer.exe or winlogon.exe. With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
4. New threats appear every day. In order to protect your PC from such (new) infections we strongly recommend you to use ESET Smart Security.
Associated AntiVirus AntiSpyware 2011 files and registry values:
Files:
In Windows XP:
- C:\Documents and Settings\[UserName]\Application Data\AntiVirus AntiSpyware 2011\
- C:\Documents and Settings\[UserName]\Application Data\AntiVirus AntiSpyware 2011\AntiVirus_AntiSpyware_2011.exe
- C:\Documents and Settings\[UserName]\Application Data\AntiVirus AntiSpyware 2011\securitymanager.exe
- C:\Documents and Settings\[UserName]\Application Data\AntiVirus AntiSpyware 2011\securityhelper.exe
- C:\Users\[UserName]\AppData\Roaming\AntiVirus AntiSpyware 2011\
- C:\Users\[UserName]\AppData\Roaming\AntiVirus AntiSpyware 2011\AntiVirus_AntiSpyware_2011.exe
- C:\Users\[UserName]\AppData\Roaming\AntiVirus AntiSpyware 2011\securitymanager.exe
- C:\Users\[UserName]\AppData\Roaming\AntiVirus AntiSpyware 2011\securityhelper.exe
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Uninstall\AntiVirus AntiSpyware 2011
- HKEY_CURRENT_USER\Software\AntiVirus AntiSpyware 2011
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "2hdpwq51skqnz"
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Security Manager"
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "AntiVirus AntiSpyware 2011"




















































