Don't Copy From This Blog...
Every once in awhile we receive emails from our readers asking for technical help or assistance in resolving computer problems caused by all sorts of malicious software, not just spyware or Trojans. Some issues require research and cannot be resolved easily. Usually we need to find a threat-specific removal utility or routine to completely remove found malware. Unfortunately, it may not work for the masses of our readers even if we believe that they have the same problem. That's why we usually respond via email. However, this time we decide to bring up this topic about quite widely used malware called Backdoor.Multi.Zaccess.gen. We thought we would explain further what it does and how to remove it from your computer.
Ok, so first let's find out what does Backdoor.Multi.Zaccess.gen actually mean? All security vendors have their malware naming standards. Well, honestly they are pretty much the same for all AV's and basically derive from the Computer Antivirus Research Organization malware naming scheme. Backdoor is a type of infection. In this case, it's a piece of malware that provides attackers with control of infected computer while attempting to remain undetected. Multi stands for cross platform. It means this malware is capable of infecting Windows and Linux or Windows and Mac OS. Zaccess is a family name. Sometimes, different security vendors use the same family names to identify closely related malware threats. But of course they can use completely different names for the same threat. For example, Microsoft identifies this threat as Sirefef whereas Kaspersky names it Zaccess (ZeroAccess). And finally, gen is an additional suffix and it basically means that malware was detected using a generic signature. Let's sum things up: Backdoor.Multi.Zaccess.gen is a proactive defense detection for suspicious behavior. We know it sounds complicated :)
How do you get infected with Backdoor.Multi.Zaccess.gen?
Cyber crooks use exploit packs to target un-patched machines. Many PC users still don't know how to update their software. Critical Windows updates are installed automatically, but that's not enough, you need to update Java, Flash and other popular software as well. Decent antivirus software is a must! In case you didn't know, you can get infected by malware just by visiting a website. You don't even need to download or install anything. Web browsers are very well-written and complex pieces of software but they still have flaws that can be utilized to run malicious software. Backdoor.Multi.Zaccess.gen infection can be also distributed through spam and using various social engineering tricks. Just like any other malicious software really.
Once installed, Backdoor.Multi.Zaccess.gen creates multiple instances of Internet Explorer (iexplore.exe). Duplicate entries can be easily seen in Task Manager. Please note that there are no visible Internet Explorer windows but the multiple instances of iexplore.exe are still running in the background.

We registered many successful attempts to establish connection with remove hosts. Internet Explorer was downloading advertisements from remote servers for some strange reasons. It might be an interesting malicious traffic monetization scheme. We will make a more thorough analysis later but it's certainly the only possible payload of this malware.

What is more, Backdoor.Multi.Zaccess.gen blocks legitimate anti-virus software and malware removal tools. It simply doesn't allow you to scan the system. Sometimes you can't even install antivirus software on the infected computer. Thankfully, there are threat-specific malware removal utilities designed to bypass malware self protection mechanisms and remove the core files from the system. Any solution for Backdoor.Multi.Zaccess.gen? Sure thing. To remove this malware infection from your computer, please follow the removal instructions below. If you have any questions, please leave a comment. Safe surfing folks!
http://spywareremovalx.blogspot.com
Backdoor.Multi.Zaccess.gen removal instructions:
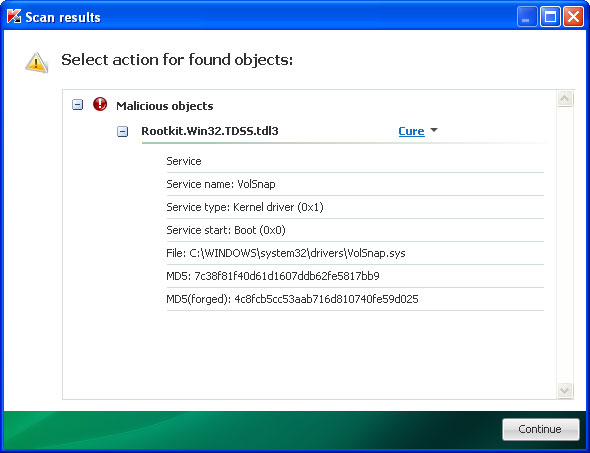
1. Download and execute TDSSKiller. Press the button Start scan for the utility to start scanning.

2. Wait for the scan and disinfection process to be over. Then click Continue. Please reboot your computer after the disinfection is over.


3. Download recommended anti-malware software (direct download) and run a full system scan to remove the remnants of this virus from your computer.
Associated Backdoor.Multi.Zaccess.gen files and registry values:
Files:
Tell your friends:
Ok, so first let's find out what does Backdoor.Multi.Zaccess.gen actually mean? All security vendors have their malware naming standards. Well, honestly they are pretty much the same for all AV's and basically derive from the Computer Antivirus Research Organization malware naming scheme. Backdoor is a type of infection. In this case, it's a piece of malware that provides attackers with control of infected computer while attempting to remain undetected. Multi stands for cross platform. It means this malware is capable of infecting Windows and Linux or Windows and Mac OS. Zaccess is a family name. Sometimes, different security vendors use the same family names to identify closely related malware threats. But of course they can use completely different names for the same threat. For example, Microsoft identifies this threat as Sirefef whereas Kaspersky names it Zaccess (ZeroAccess). And finally, gen is an additional suffix and it basically means that malware was detected using a generic signature. Let's sum things up: Backdoor.Multi.Zaccess.gen is a proactive defense detection for suspicious behavior. We know it sounds complicated :)
How do you get infected with Backdoor.Multi.Zaccess.gen?
Cyber crooks use exploit packs to target un-patched machines. Many PC users still don't know how to update their software. Critical Windows updates are installed automatically, but that's not enough, you need to update Java, Flash and other popular software as well. Decent antivirus software is a must! In case you didn't know, you can get infected by malware just by visiting a website. You don't even need to download or install anything. Web browsers are very well-written and complex pieces of software but they still have flaws that can be utilized to run malicious software. Backdoor.Multi.Zaccess.gen infection can be also distributed through spam and using various social engineering tricks. Just like any other malicious software really.
Once installed, Backdoor.Multi.Zaccess.gen creates multiple instances of Internet Explorer (iexplore.exe). Duplicate entries can be easily seen in Task Manager. Please note that there are no visible Internet Explorer windows but the multiple instances of iexplore.exe are still running in the background.

We registered many successful attempts to establish connection with remove hosts. Internet Explorer was downloading advertisements from remote servers for some strange reasons. It might be an interesting malicious traffic monetization scheme. We will make a more thorough analysis later but it's certainly the only possible payload of this malware.

What is more, Backdoor.Multi.Zaccess.gen blocks legitimate anti-virus software and malware removal tools. It simply doesn't allow you to scan the system. Sometimes you can't even install antivirus software on the infected computer. Thankfully, there are threat-specific malware removal utilities designed to bypass malware self protection mechanisms and remove the core files from the system. Any solution for Backdoor.Multi.Zaccess.gen? Sure thing. To remove this malware infection from your computer, please follow the removal instructions below. If you have any questions, please leave a comment. Safe surfing folks!
http://spywareremovalx.blogspot.com
Backdoor.Multi.Zaccess.gen removal instructions:
1. Download and execute TDSSKiller. Press the button Start scan for the utility to start scanning.

2. Wait for the scan and disinfection process to be over. Then click Continue. Please reboot your computer after the disinfection is over.


3. Download recommended anti-malware software (direct download) and run a full system scan to remove the remnants of this virus from your computer.
Associated Backdoor.Multi.Zaccess.gen files and registry values:
Files:
- C:\Documents and Settings\All Users\Application Data\0Hh3oQ7q.exe
- C:\WINDOWS\TEMP\qllmdq\setup.exe
Tell your friends: