Don't Copy From This Blog...
Windows Oversight Center is a fake anti-virus program that pretends to scan your computer for viruses and system/registry errors. It reports non-existent viruses and asks you to register the program in order to cleanup the computer. Windows Oversight Center periodically displays fake security alerts and may even point your web browser to websites that aren't necessarily the kind that you might want popping up on your computer screen. However, most of the time, the rogue program just shut downs the web browser. You can't download anything and you can't run anti-virus software as well because it blocks pretty much everything on the infected computer. It displays a fake warning claiming that the program was infected by a virus and was closed to prevent system errors and data leak. Although, it looks like an authentic Microsoft product, Windows Oversight Center is actually a scam. Thankfully, we've got the removal instructions to help you to remove Windows Oversight Center.
Windows Oversight Center is distributed through the use of JavaScript-based fake virus scanners in attempt to trick you into thinking that you have security problems on your PC. The malware attackers also use a lot of social engineering and the fake Microsoft Security Essentials Alert to install the rogue program.

Once installed, Windows Oversight Center displays the fake Safe Boot Screen and then loads up the fake virus scanner.

There are six main components, i.e., computer safety, network security, hard disk optimization, etc. The fake program also uses Windows logo and Microsoft genuine software notification. My guess is that the scammers are doing this as a further incentive for you to purchase Windows Oversight Center. DO NOT pay for this phony AV program. If you you purchase it, you will subjected to monetary theft, or in a worst-case example, ID Theft. There is no guarantee that your credit card details aren't going to be sold to other third parties. So, if you have already purchased, you should contact your credit card company immediately and dispute the charges. Then, get rid of Windows Oversight Center. Please follow the removal instructions below. If you have any further questions, please leave a comment. Good luck and be safe online!
Windows Oversight Center removal instructions:
1. Rename the main executable of the rogue program:
In Windows XP:
C:\Documents and Settings\[UserName]\Application Data\[SET OF RANDOM CHARACTERS].exe
C:\Documents and Settings\[UserName]\Application Data\Microsoft\[SET OF RANDOM CHARACTERS].exe
In Windows Vista/7:
C:\Users\[UserName]\AppData\Roaming\[SET OF RANDOM CHARACTERS].exe
C:\Users\[UserName]\AppData\Roaming\Microsoft\[SET OF RANDOM CHARACTERS].exe

Alternate location:

Look for xmrmuy or similar file and rename it to malware. Then restart your computer. This should disable the rogue program. After reboot, please continue with the rest of the removal process. NOTE: By default, Application Data folder is hidden. If you can find it, please read Show Hidden Files and Folders in Windows.
2. Download shell-fix.reg. Double-click to run it. Click "Yes" when it asks if you want to add the information to the registry. This file will fix the Windows Shell entry.
3. Download free anti-malware software from the list below and run a full system scan.
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe or winlogon.exe With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
4. New threats appear every day. In order to protect your PC from such (new) infections we strongly recommend you to use ESET NOD32 Antivirus.
Alternate Windows Oversight Center removal instructions (in Safe Mode with Networking):
1. Reboot your computer is "Safe Mode with Networking". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key. Read more detailed instructions here: http://www.computerhope.com/issues/chsafe.htm
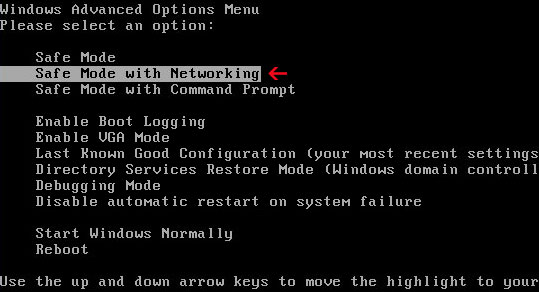
NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. Download free anti-malware software from the list below and run a full system scan.
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe or winlogon.exe With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
3. New threats appear every day. In order to protect your PC from such (new) infections we strongly recommend you to use ESET NOD32 Antivirus.
Associated files and registry values:
Files:
In Windows XP:
- C:\Documents and Settings\[UserName]\Application Data\[SET OF RANDOM CHARACTERS].exe
- C:\Documents and Settings\[UserName]\Application Data\Microsoft\[SET OF RANDOM CHARACTERS].exe
- C:\Users\[UserName]\AppData\Roaming\[SET OF RANDOM CHARACTERS].exe
- C:\Users\[UserName]\AppData\Roaming\Microsoft\[SET OF RANDOM CHARACTERS].exe
- HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon "Shell" = '%UserProfile%\Application Data\[SET OF RANDOM CHARACTERS].exe'
- HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon "Shell" = '%UserProfile%\Application Data\Microsoft\[SET OF RANDOM CHARACTERS].exe'
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\egui.exe "Debugger" = 'svchost.exe'
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ekrn.exe "Debugger" = 'svchost.exe'
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msascui.exe "Debugger" = 'svchost.exe'
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmpeng.exe "Debugger" = 'svchost.exe'
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msseces.exe "Debugger" = 'svchost.exe'

















0 comments:
Post a Comment