Don't Copy From This Blog...
Security Suite is a fake anti-spyware program that gives exaggerated or false reports of threats on the computer. Most of the time, this peace of malware has to be manually installed. Malware authors and distributors use misleading social engineering schemes, fake online scanners, spam emails and other methods to spread their malicious code and infect as many computers as possible. Security Suite is a typical rogue anti-spyware scanner. Once installed, it will scan your computer and display a list of fake infections. You are not allowed to remove those infections, unless you pay for a full version of the program. And that's the whole point; it attempts to get you to pay for fake anti-virus software. Please don't buy this bogus program. If you have already purchased it then contact your credit card company's fraud department immediately. It goes without saying, that you should remove Security Suite from your computer as soon as possible. Thankfully we've got the instructions to help you remove this virus.
(Thanks to rogueamp for this video)
When Security Suite is active, it will display many fake security warnings and state that your computer is seriously infected with spyware, adware and other malware. You can safely ignore those fake security alerts. The biggest problem is that SecuritySuite blocks legitimate anti-spyware and antivirus programs. When you attempt to run a program, Security Suite closes it and then display the following error message:
Security warning
Application cannot be executed. The file [file_name].exe is infected. Do you want to activate your antivirus software now?

Furthermore, Security Suite will configure Windows to use a proxy server. It will intercept the request and display fake security warnings.


Other fake security warnings:


SecuritySuite is from the same family as Antivir Solution Pro, AV Security Suite, Antispyware Soft and Antivirus Soft scareware.
Last, but not least, this fake program can be installed with TDSS rootkit. You should scan your computer with TDSSKiller utility after you remove the rogue program. For more information please read TDSS, Alureon, Tidserv, TDL3 removal instructions using TDSSKiller utility. What is more, you should also purge all old system restore points and create a new one. If you don't know how to delete system restore points then please follow the steps in the Microsoft knowledgebase article http://support.microsoft.com/kb/310405.
As you can see, Security Suite is nothing more but a scam. It wants to make you think that your computer is infected, but the only real infection is the rogue program itself. Without a doubt, you should uninstall Security Suite from the system upon detection. You can remove it manually, but we strongly recommend you to use anti-virus or anti-spyware program. Please follow the removal instructions below. If you have any questions or additional information about Security Suite, please leave a comment. Good luck and be safe!
Security Suite removal instructions (in Safe Mode with Networking):
1. Reboot your computer is "Safe Mode with Networking". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key. Read more detailed instructions here: http://www.computerhope.com/issues/chsafe.htm
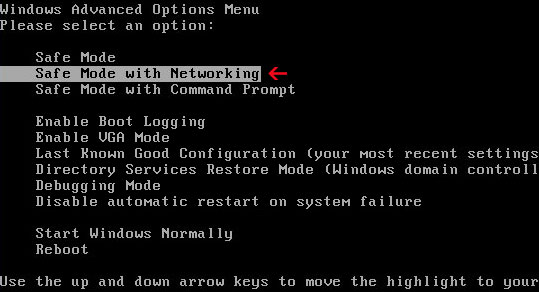
NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. Launch Internet Explorer. In Internet Explorer go to: Tools->Internet Options->Connections tab.
Click Lan Settings button and uncheck the checkbox labeled Use a proxy server for your LAN. Click OK.

3. Download at least one anti-malware program from the list below and run a full system scan.
NOTE: before saving the selected program onto your computer, please rename the installer to winlogon.exe or iexplore.exe. With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
4. New threats appear every day. In order to protect your PC from such (new) infections we strongly recommend you to use ESET Smart Security.
Alternative Security Suite removal instructions using HijackThis (in Normal mode):
1. Download iexplore.exe (NOTE: iexplore.exe file is renamed HijackThis tool from TrendMicro).
Launch the iexplore.exe and click "Do a system scan only" button.
If you can't open iexplore.exe file then download explorer.scr and run it.
2. Search for similar entries in the scan results:
R1 – HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings,ProxyServer = http=127.0.0.1
O4 – HKLM\..\Run: [mreqslst] C:\Documents and Settings\[User]\Local settings\Application data\rhfrlps\ncfdskshdw.exe
O4 – HKCU\..\Run: [mreqslst] C:\Documents and Settings\[User]\Local settings\Application data\rhfrlps\ncfdskshdw.exe
The process name will be different in your case [SET OF RANDOM CHARACTERS]shdw.exe, located in C:\Documents and Settings\[UserName]\Local settings\Application data\
Select all similar entries and click once on the "Fix checked" button. Close HijackThis tool.
3. Delete the follow file C:\WINDOWS\Prefetch\[RANDOM]SHDW.EXE-[RANDOM].pf if exists.
4. Download at least one anti-malware program from the list below and run a full system scan.
NOTE: before saving the selected program onto your computer, please rename the installer to winlogon.exe or iexplore.exe. With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
5. New threats appear every day. In order to protect your PC from such (new) infections we strongly recommend you to use ESET Smart Security.
Security Suite associated files and registry values:
Files:
- %UserProfile%\Local Settings\Application Data\SET OF RANDOM CHARACTERS]\
- %UserProfile%\Local Settings\Application Data\SET OF RANDOM CHARACTERS]\SET OF RANDOM CHARACTERS]shdw.exe
- C:\Users\User\AppData\Local\[SET OF RANDOM CHARACTERS] (Windows Vista & Windows 7)
- C:\WINDOWS\Prefetch\[RANDOM]SHDW.EXE-[RANDOM].pf (if exists)
- HKEY_CURRENT_USER\Software\wnxmal
- HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Download "RunInvalidSignatures" = "1"
- HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\PhishingFilter "Enabled" = "0"
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "ProxyOverride" = ""
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "ProxyServer" = "http=127.0.0.1:6522"
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Associations "LowRiskFileTypes" = ".exe"
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments "SaveZoneInformation" = "1"
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "
" - HKEY_CURRENT_USER\Software\Microsoft\Windows\ShellNoRoam\MUICache "%UserProfile%\Desktop\flash_player_installer\flash_player_installer.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run "
" - HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Download "CheckExeSignatures" = "no"
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "ProxyEnable" ="1"

















0 comments:
Post a Comment