Don't Copy From This Blog...
It's been a while since we've last seen a rogue security program from scareware families other that Fakevimes and Winwebsec. Ransomware applications have been roaming around the net for a while replacing (only partly) fake antivirus programs. Our guess is that ransomware scams became more profitable than rogue AVs. However, yesterday we stumbled upon a new rogue anti-virus program called Windows Ultra Antivirus which only proves that affiliate scareware networks are still active and not leaving anytime soon.
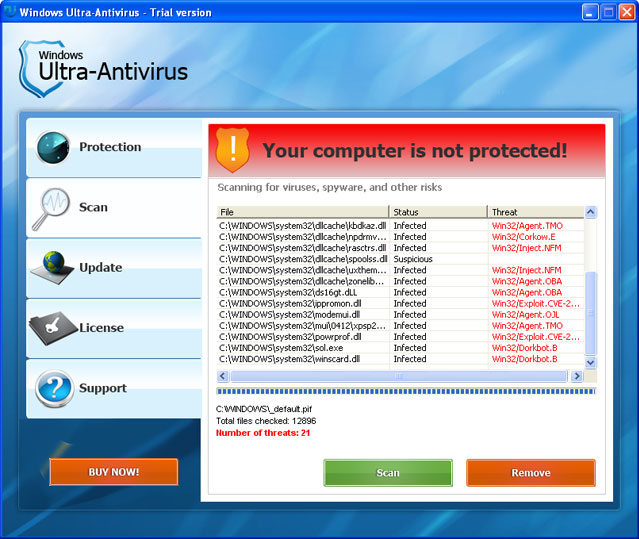
Windows Ultra-Antivirus is not a particularly nasty piece of malware. It's a typical fake antivirus program which claims that your computer is infected with viruses. Once installed, the rogue program pretends to scan your machine for malicious software. It randomly displays genuine Windows files and assigns assumed malware infections for each of those files. The rogue program rarely detects less then ten malware infections even on a perfectly clean computer with freshly installed Windows on it.
Unlike most fake antivirus programs, Windows Ultra Antivirus provides short threat descriptions for all the infections found during the scan. Not sure why malware authors did that but again we can guess they are trying to drive more sales by adding some extra reliability to their useless software.
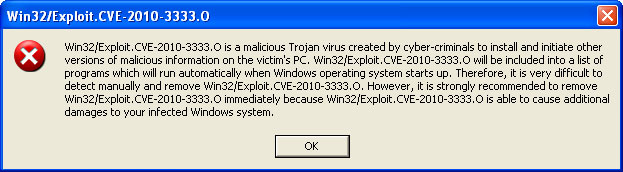
Win32/Exploit.CVE-2010-3333.0 threat description:
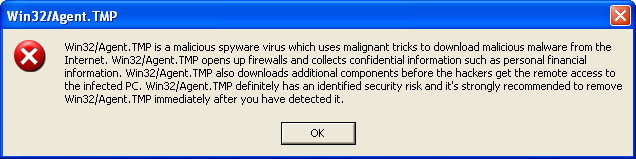
Win32/Agent.TMP threat description:
Windows Ultra Antivirus is promoted through the use of fake online virus scanners and Trojan horses that masquerade as a legitimate Microsoft updates. The rogue application is configured to run automatically when Windows starts. The most worrying part is a rookit infection which comes bundled with this fake antivirus program. The malicious randomly named .sys file is dropped in C:\WINDOWS\system32\drivers folder. The file is locked so you can’t remove it manually.
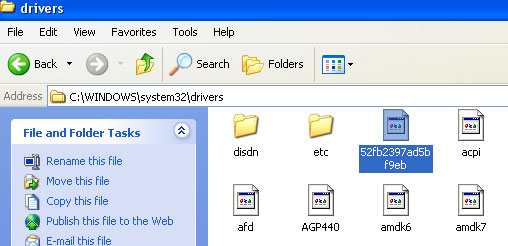
In our case, the rootkit was detected as Gen:Variant.Zusy.8505 by GData ((Engine A).
Startup properties:
HKLM\SYSTEM\ControlSet001\Services\52fb2397ad5bf9eb\
The Windows Ultra Antivirus itself was detected as Trojan.FakeAlert.CYD, BackDoor.Bulknet.713, and Trojan-Dropper!IK by three different antivirus engines.
Normally, in order to remove found malware, victims are asked to purchase rogue AV programs. Windows Ultra-Antivirus scam works the same way but the problem is that at least at the time we tested this scareware, the payment page was unavailable.
hxxp://www.zokaisoft.com/payments/buynow.php?vendorId=1
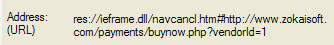
So, it’s either a sign of a poorly organized scareware attack or they have some serious problems with payment processing.
Zokaisoft.com was registered by Aleksandr Bakcheev from Russia just a few weeks ago. But the whois information is probably false. We don't think such person even exists, unless cyber criminals used stolen credit card and personal details to register this domain.
So, what to do if you got infected by this annoying malware? First and foremost, do not attempt to remove Windows Ultra Antivirus manually. If you don't remove all malware components, malware authors can do anything while on your computer including reading your key strokes and getting personal identification information. To remove this malware from your computer properly, please follow the removal instructions below. Comments and questions are welcome. Good luck!
Windows Ultra Antivirus removal instructions:
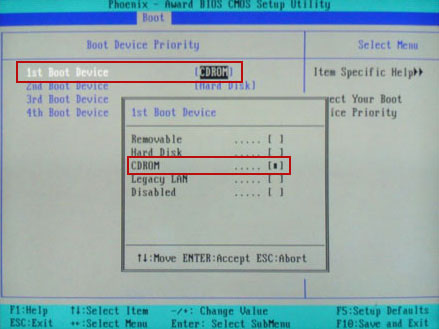
1. First of all, we need to remove the rootkit. Download TDSSKiller and save it on your desktop.
2. Double-click on it to start TDSSKiller. NOTE: sometimes, rootkits block this utility to avoid removal. If you can't run this utility, simply rename tdsskiller.exe to iexplore.exe and run it again.
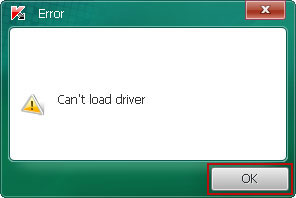
3. Once started, TDSSKiller may display an error message stating that it Can't Load Driver. Don't worry about that, simply click OK to continue.
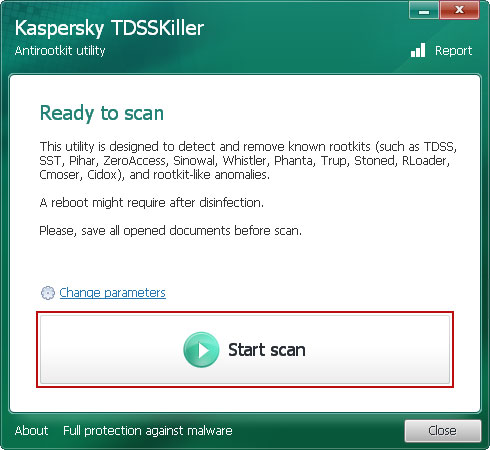
4. Click on the Start Scan button to begin scanning your computer for rootkits.
5. When the scan is over, the utility outputs a list of detected objects with description. You should see a locked service which is the actual rootkit we need to remove.
Choose to Delete this rootkit and click on the Continue to remove delete the rootkit.
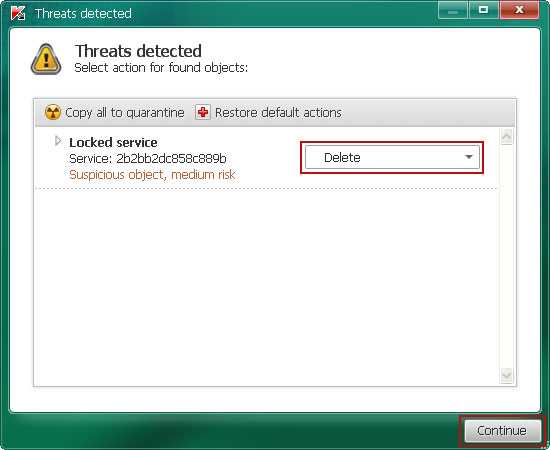
6. A reboot might require after disinfection. Click on the Reboot computer button.
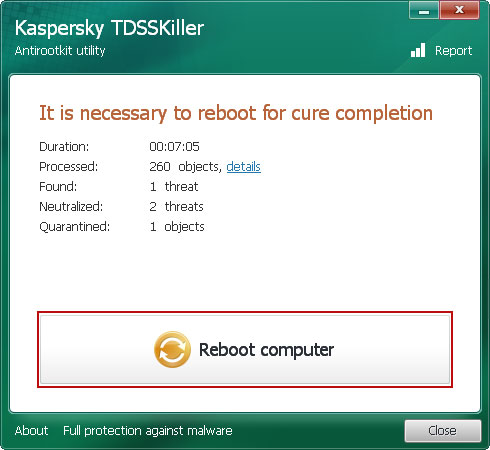
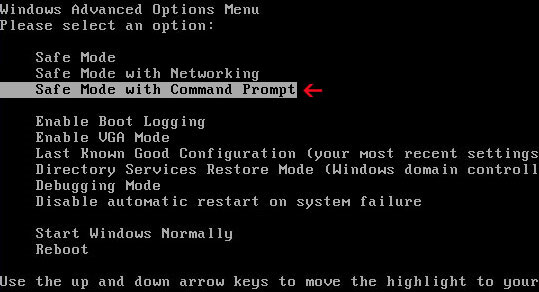
7. TDSSKiller will now reboot your computer, but instead going into normal Windows mode reboot your computer is "Safe Mode with Networking". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key.
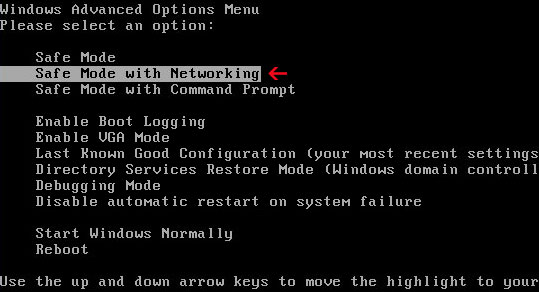
NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
8. Download recommended anti-malware software (Spyware Doctor) and run a full system scan to remove this virus and associated malware from your computer.
NOTE: don't forget to update anti-malware software before scanning your computer.
Associated Windows Ultra Antivirus files and registry values:
Files:
Windows XP:

Windows Ultra-Antivirus is not a particularly nasty piece of malware. It's a typical fake antivirus program which claims that your computer is infected with viruses. Once installed, the rogue program pretends to scan your machine for malicious software. It randomly displays genuine Windows files and assigns assumed malware infections for each of those files. The rogue program rarely detects less then ten malware infections even on a perfectly clean computer with freshly installed Windows on it.
Unlike most fake antivirus programs, Windows Ultra Antivirus provides short threat descriptions for all the infections found during the scan. Not sure why malware authors did that but again we can guess they are trying to drive more sales by adding some extra reliability to their useless software.
Win32/Exploit.CVE-2010-3333.0 threat description:

Win32/Agent.TMP threat description:

Windows Ultra Antivirus is promoted through the use of fake online virus scanners and Trojan horses that masquerade as a legitimate Microsoft updates. The rogue application is configured to run automatically when Windows starts. The most worrying part is a rookit infection which comes bundled with this fake antivirus program. The malicious randomly named .sys file is dropped in C:\WINDOWS\system32\drivers folder. The file is locked so you can’t remove it manually.

In our case, the rootkit was detected as Gen:Variant.Zusy.8505 by GData ((Engine A).
Startup properties:
HKLM\SYSTEM\ControlSet001\Services\52fb2397ad5bf9eb\
The Windows Ultra Antivirus itself was detected as Trojan.FakeAlert.CYD, BackDoor.Bulknet.713, and Trojan-Dropper!IK by three different antivirus engines.
Normally, in order to remove found malware, victims are asked to purchase rogue AV programs. Windows Ultra-Antivirus scam works the same way but the problem is that at least at the time we tested this scareware, the payment page was unavailable.
hxxp://www.zokaisoft.com/payments/buynow.php?vendorId=1

So, it’s either a sign of a poorly organized scareware attack or they have some serious problems with payment processing.
Zokaisoft.com was registered by Aleksandr Bakcheev from Russia just a few weeks ago. But the whois information is probably false. We don't think such person even exists, unless cyber criminals used stolen credit card and personal details to register this domain.
So, what to do if you got infected by this annoying malware? First and foremost, do not attempt to remove Windows Ultra Antivirus manually. If you don't remove all malware components, malware authors can do anything while on your computer including reading your key strokes and getting personal identification information. To remove this malware from your computer properly, please follow the removal instructions below. Comments and questions are welcome. Good luck!
Windows Ultra Antivirus removal instructions:
1. First of all, we need to remove the rootkit. Download TDSSKiller and save it on your desktop.
2. Double-click on it to start TDSSKiller. NOTE: sometimes, rootkits block this utility to avoid removal. If you can't run this utility, simply rename tdsskiller.exe to iexplore.exe and run it again.
3. Once started, TDSSKiller may display an error message stating that it Can't Load Driver. Don't worry about that, simply click OK to continue.

4. Click on the Start Scan button to begin scanning your computer for rootkits.

5. When the scan is over, the utility outputs a list of detected objects with description. You should see a locked service which is the actual rootkit we need to remove.
Choose to Delete this rootkit and click on the Continue to remove delete the rootkit.

6. A reboot might require after disinfection. Click on the Reboot computer button.

7. TDSSKiller will now reboot your computer, but instead going into normal Windows mode reboot your computer is "Safe Mode with Networking". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key.

NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
8. Download recommended anti-malware software (Spyware Doctor) and run a full system scan to remove this virus and associated malware from your computer.
NOTE: don't forget to update anti-malware software before scanning your computer.
Associated Windows Ultra Antivirus files and registry values:
Files:
Windows XP:
- C:\Windows\System32\[SET OF RANDOM CHARACTERS].exe
- C:\Windows\System32\drivers\[SET OF RANDOM CHARACTERS].sys
- HHKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "[SET OF RANDOM CHARACTERS]"