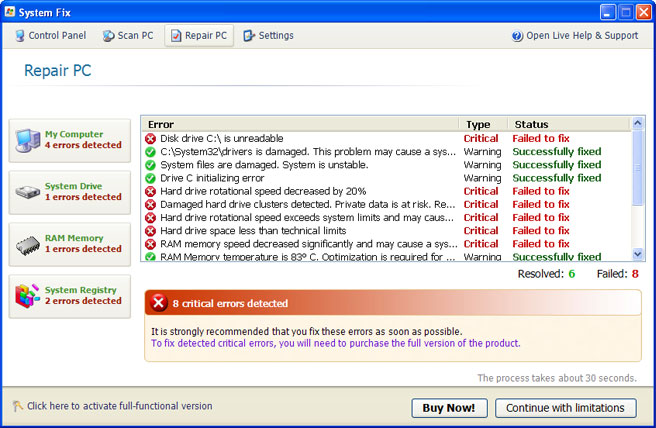
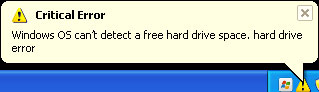
Cloud AV 2012 is a rogue antivirus program that claims to find malicious software on your computer. The rogue program disables certain Windows utilities and blocks genuine security products. It launches itself every time your PC is turned on and pretends to scan the system for malware. It is worth mentioning, however, that this fake AV reports exactly the same infections on different computers:
Trojan.JBS.Ghost,
Trojan-Downloader.JS.Remora,
Net-Worm.Win32.Kido.ih and other stuff. Yeah, I know it's possible but not probably, right? So, basically, Cloud AV 2012 malware is playing on your fears to try to sell you completely BS security product. If you have fallen for the scam and have paid for the rogue program you should issue chargebacks through your credit card company. That's the only way to get your money back, besides, too many chargebacks will probably result in the merchant losing the ability to accept credit card payments. That's a good thing, isn't it? Then you need to remove Cloud AV 2012 and associated malware from your computer. To do so, please follow the removal instructions below.
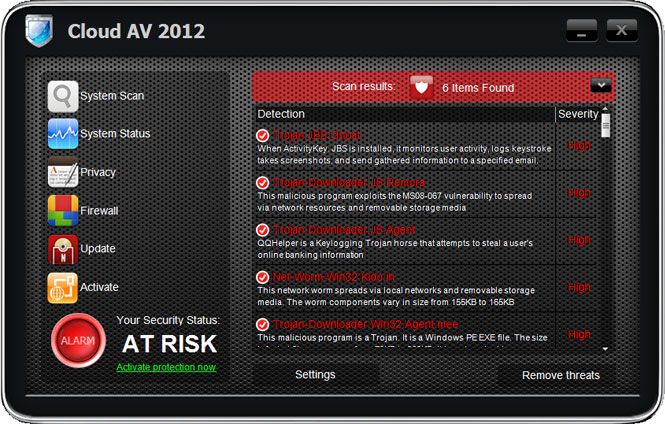
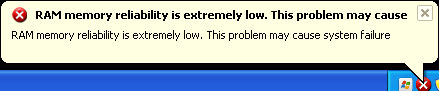
Usually, such fake AVs as Cloud AV 2012 drive people nuts, especially because of never ending alerts and notifications about critical threats, etc.
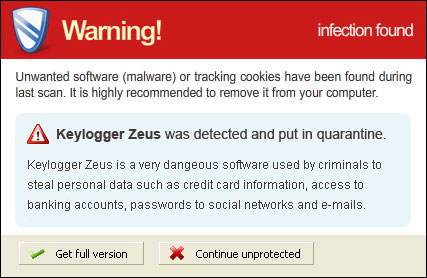
However, they are not so dangerous after all and I think shouldn't be compared to more sophisticated malware, rootkits, worms or viruses. It's just well designed but useless application which reports non-existent infections. That's all. Then bad news is, however, that Cloud AV 2012 comes bundled with
Trojans and sometimes even
rootkits. There are usually a number of Trojans that can download additional malcode onto the infected computer and rootkits may hide/block legitimate antivirus programs. But that's not all, the rogue program modifies Windows Hosts file to redirect internet traffic to either infected or sponsored websites involved in click fraud schemes.
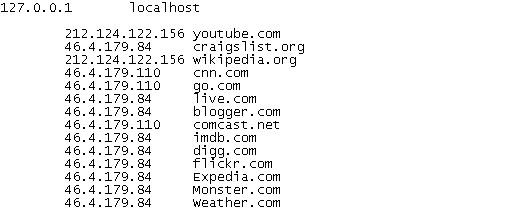
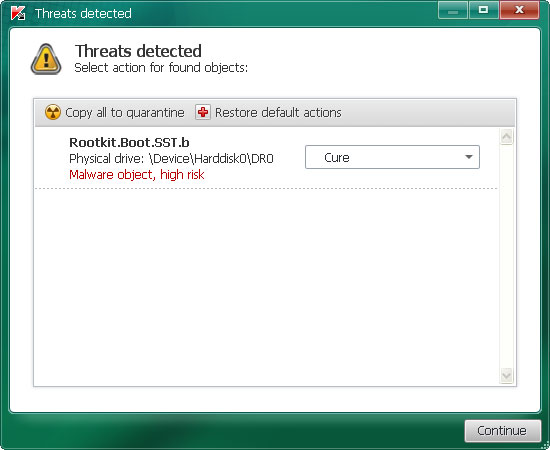
So there you go. I know it sounds like a lot of job, removing Cloud AV 2012 and associated malware is not that difficult after all. First, run rootkit removal utility. Then scan your computer with recommend anti-malware program. Finally, restore Windows Hosts file using Fix it utility. You may even use this debugged registration key 9992665263 to make your life and removal procedure a little bit easier. Just follow the steps in the removal guide below. If you need extra help removing it, please leave a comment below. Good luck and be safe online!
http://spywareremovalx.blogspot.com
Cloud AV 2012 removal instructions:1. First of all, download and run
ZeroAccess/Sirefef/MAX++ removal tool. (works on 32-bit systems only! If you have 64-bit system, proceed to the next step)
2. Then use
TDSSKiller. If you can't run it (rogue av blocks it), rename
tdsskiller to
winlogon and run the utility again.
3. And finally, download recommended
anti-malware software (Spyware Doctor) and run a full system scan to remove this virus from your computer.
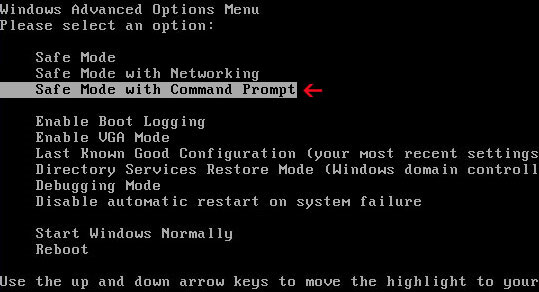
If you can't download it, please reboot your computer is "
Safe Mode with Networking". As the computer is booting tap the "
F8 key" continuously which should bring up the "
Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key. That's It!
Read more detailed instructions here:
http://www.computerhope.com/issues/chsafe.htm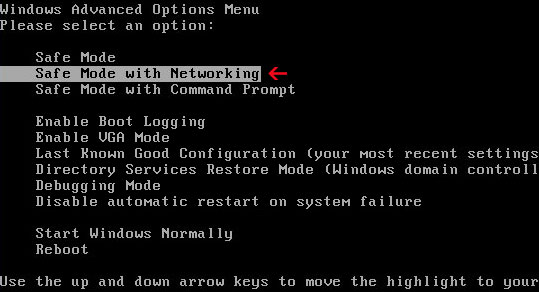
NOTE:
Login as the same user you were previously logged in with in the normal Windows mode.
4. To reset the Hosts file back to the default automatically, download and run
Fix it and follow the steps in the Fix it wizard.
Manual Cloud AV 2012 removal guide:1. Right-click on
Cloud AV 2012 icon and select
Properties. Then select
Shortcut tab.
The location of the malware is in the
Target box.
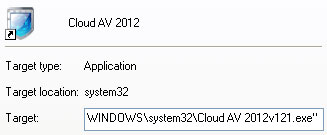
2. In our case the malicious file was located in C:\Windows\System32 folder. Select the malicious file, rename it and change a file name extension.
Original file:
Cloud AV 2012v121.exe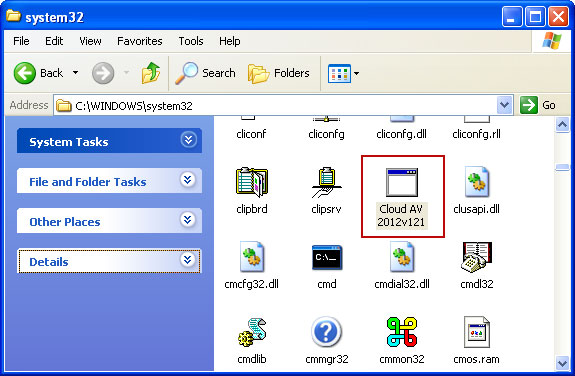
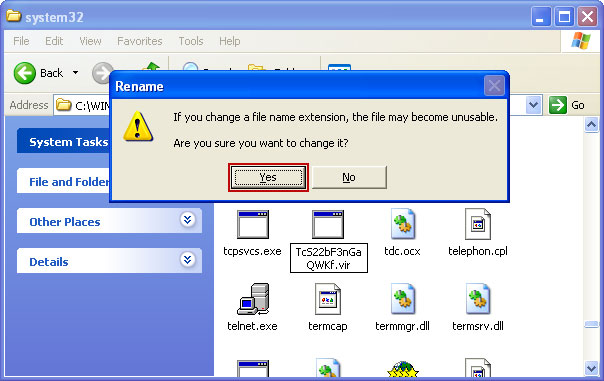
Renamed file:
TcS22bF3nGaQWKf.vir (you may change only the file name and leave file extension .exe)
3. Restart your computer. After a reboot, download free anti-malware software from the list below and run a full system scan.
4. First, use
TDSSKiller. Then download recommended
anti-malware software (Spyware Doctor) and run a full system scan to remove this virus from your computer.
5. To reset the Hosts file back to the default automatically, download and run
Fix it and follow the steps in the Fix it wizard.
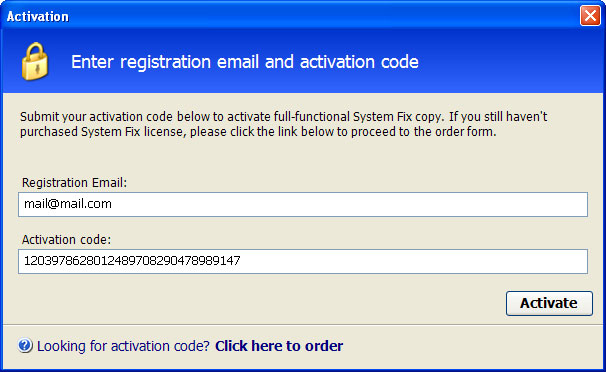
Manual activation and Cloud AV 2012 removal:1. Choose to remove threats and manually activate the rogue program. Enter one of the following codes to activate Cloud AV 2012.
9992665263
1148762586
1171249582
1186796371
1196121858
2. Download recommended
anti-malware software (Spyware Doctor) and run a full system scan to remove this virus from your computer.
Associated Cloud AV 2012 files and registry values:Files:
- C:\WINDOWS\system32\Cloud AV 2012v121.exe
- %AppData%\dwme.exe
- %DesktopDir%\Cloud AV 2012.lnk
- %Programs%\Cloud AV 2012\Cloud AV 2012.lnk
- %Programs%\Cloud AV 2012
Registry values:
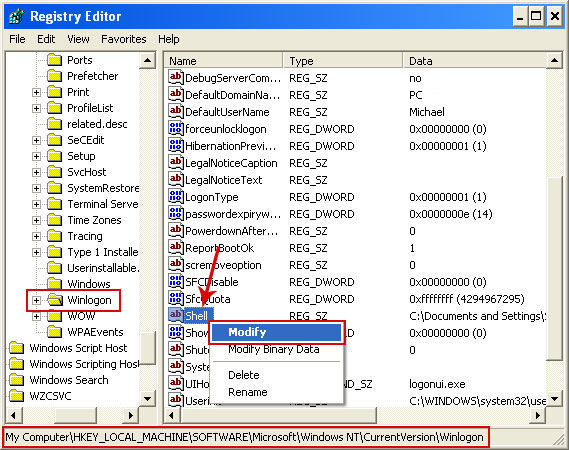
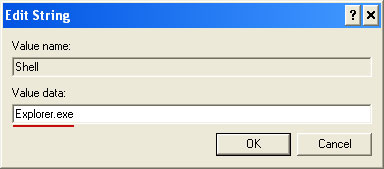
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run "[SET OF RANDOM CHARACTERS]"
Share this information with your friends: