Don't Copy From This Blog...
DomaIQ is adware that will display pop-up advertisements on your computer. Most antivirus engines detect it as Adware.DomaIQ. Other security applications flag it simply as PUP (Potentially Unwanted Program), for example, PUP.DomaIQ or PUP.FakeFlash.Domaiq. When the program is executed, it drops a few .exe files in %Temp% folder, usually launcher4.exe and launcher.exe. It also creates .zip archives containing DomaIQ10.exe and DomaIQ.exe files. Have you found that you suddenly have an issue with seemingly endless pop-up windows when you are using your computer? Do you seem to be bombarded with full page screens showing explicit photos, dubious weight loss or adult content websites when you are browsing the internet? If you answered yes to either or both of these questions it is very likely that your computer has been infected with this adware. Computer experts have estimated that anywhere from between 60 to 80% of all home computers that are connected to the internet have some sort of adware – or the other malware that it is often bundled with, spyware, installed and the scary part is that the majority of people have no idea how the adware even found its way on to their computer in the first place. This particular adware usually masquerades as an installer of legitimate software, for instance Flash Player Update. However, many legitimate applications use DomaIQ monitization platform to monetize their software, so it's not necessarily misleading or malicious all the time.
DomaIQ by Tuguu SLU is easier to spot than spyware and if you’re seeing pop up boxes, your computer is running sluggishly or you’re being directed to websites you’ve no interest in it’s fairly safe to say that you want to know how to get rid of it and you’d like to know how you can prevent it from happening again in the future. This article attempts to answer those questions but before we do that let’s look a little closer at what adware and spyware actually are.
The definition of adware is that it is any program that is running on your PC that connects to the internet and then uses your computer to host adverts - and perhaps to even transmit adverts to other computers. These ads take the form of those annoying little pop-ups, banners and flashing ads. They will appear every time you connect to the internet - and all of them are trying their hardest to get you to click on them. Adware may also install additional components on compromised computer, for example malicious web browser extensions or rogue software optimization tools.
There are a number of routes that DomaIQ adware can take to infect your computer system. It could have been when you were installing another program online, or when you clicked a dialogue box in your internet browser and unwittingly authorized this rogue message to install the adware. Adware often packaged with a great number of free software programs and it is highly likely that the adware was installed without your knowledge when you were installing a program that you did actually want.
You should always exercise extreme caution when downloading files, shareware and programs – even reputable ones – from the internet as these can often be bundled with adware. Fake Flash player update adware applications are still going strong. Make sure you trust the program and its software author, and think to yourself whether you really need it in the first place.
Another thing to watch out for is the fake dialogue boxes mentioned earlier; these will often give you a ‘yes’ or ‘no’ option concerning a command – clicking on either could install the adware so make sure you close them with the red ‘x’ in the top right hand corner instead.
The key to avoiding DomaIQ adware is to stay vigilant and to not download programs from unknown sources. Last, but not least, some users get an error message every time they try the uninstall DomaIQ. If such case, use DomaIQ Uninstaller. Please note, you after you remove DomaIQ from your computer, you will have to remove DomaIQ Uninstaller as well. Please follow the removal instructions below. If you have any questions, please leave a comment below. Good luck and be safe online!
Written by Michael Kaur, http://spywareremovalx.blogspot.com
DomaIQ adware removal instructions:
1. First of all, download recommended anti-malware software and run a full system scan. It will detect and remove this adware from your computer. You may then follow the manual removal instructions below to remove the leftover traces of this adware. Hopefully you won't have to do that.
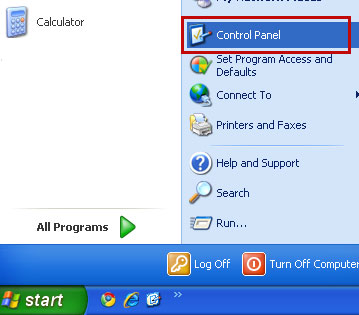
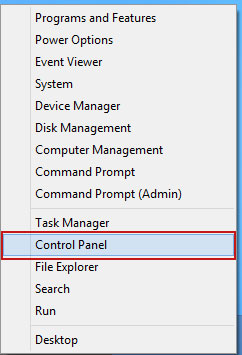
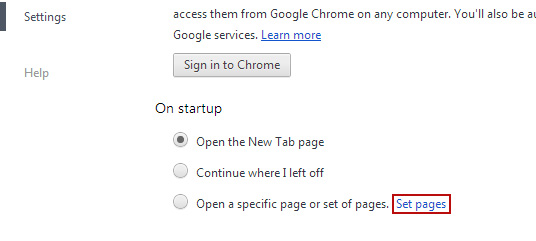
2. Go to My Computer or Computer (depending on what OS your using Windows XP, Vista or Windows 7/8).
3. Go to Program Files, then open DomaIQ Uninstaller folder and run Uninstaller.exe. Follow the on-screen instructions.
Uninstaller: "C:\Program Files\DomaIQ Uninstaller\uninstaller.exe"
4. Now, delete the DomaIQ Uninstaller:
a) Go to DomalQ Uninstaller and drag that folder to the recycle bin on your desktop.
b) Right Click on Recycle Bin and Click empty Recycle Bin.
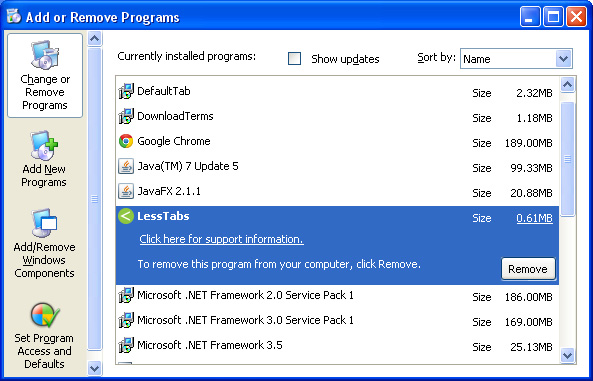
c) Then open Add/Remove programs in the Control Panel and now you can safely remove the remaining path.
d) Restart your computer.
DomaIQ Adware detection.
DomaIQ by Tuguu SLU is easier to spot than spyware and if you’re seeing pop up boxes, your computer is running sluggishly or you’re being directed to websites you’ve no interest in it’s fairly safe to say that you want to know how to get rid of it and you’d like to know how you can prevent it from happening again in the future. This article attempts to answer those questions but before we do that let’s look a little closer at what adware and spyware actually are.
The definition of adware is that it is any program that is running on your PC that connects to the internet and then uses your computer to host adverts - and perhaps to even transmit adverts to other computers. These ads take the form of those annoying little pop-ups, banners and flashing ads. They will appear every time you connect to the internet - and all of them are trying their hardest to get you to click on them. Adware may also install additional components on compromised computer, for example malicious web browser extensions or rogue software optimization tools.
There are a number of routes that DomaIQ adware can take to infect your computer system. It could have been when you were installing another program online, or when you clicked a dialogue box in your internet browser and unwittingly authorized this rogue message to install the adware. Adware often packaged with a great number of free software programs and it is highly likely that the adware was installed without your knowledge when you were installing a program that you did actually want.
DomaIQ by Tuguu installer.
You should always exercise extreme caution when downloading files, shareware and programs – even reputable ones – from the internet as these can often be bundled with adware. Fake Flash player update adware applications are still going strong. Make sure you trust the program and its software author, and think to yourself whether you really need it in the first place.
Another thing to watch out for is the fake dialogue boxes mentioned earlier; these will often give you a ‘yes’ or ‘no’ option concerning a command – clicking on either could install the adware so make sure you close them with the red ‘x’ in the top right hand corner instead.
The key to avoiding DomaIQ adware is to stay vigilant and to not download programs from unknown sources. Last, but not least, some users get an error message every time they try the uninstall DomaIQ. If such case, use DomaIQ Uninstaller. Please note, you after you remove DomaIQ from your computer, you will have to remove DomaIQ Uninstaller as well. Please follow the removal instructions below. If you have any questions, please leave a comment below. Good luck and be safe online!
Written by Michael Kaur, http://spywareremovalx.blogspot.com
DomaIQ adware removal instructions:
1. First of all, download recommended anti-malware software and run a full system scan. It will detect and remove this adware from your computer. You may then follow the manual removal instructions below to remove the leftover traces of this adware. Hopefully you won't have to do that.
2. Go to My Computer or Computer (depending on what OS your using Windows XP, Vista or Windows 7/8).
3. Go to Program Files, then open DomaIQ Uninstaller folder and run Uninstaller.exe. Follow the on-screen instructions.
Uninstaller: "C:\Program Files\DomaIQ Uninstaller\uninstaller.exe"
4. Now, delete the DomaIQ Uninstaller:
a) Go to DomalQ Uninstaller and drag that folder to the recycle bin on your desktop.
b) Right Click on Recycle Bin and Click empty Recycle Bin.
c) Then open Add/Remove programs in the Control Panel and now you can safely remove the remaining path.
d) Restart your computer.