Don't Copy From This Blog...
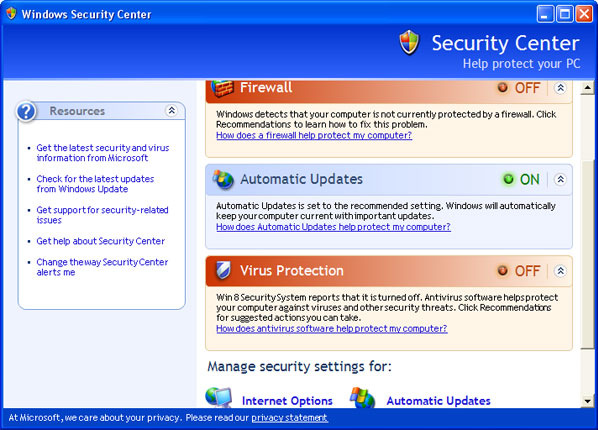
So, you got the click.get-amazing-results.com browser hijacker and you can't remove it. This can be a sigh of malware or potentially unwanted browser helper object. In most cases, I have to assume that it’s some sort of malicious software, specifically a Trojan horse or a rootkit. The last time a got a computer infected with click.get-amazing-results redirect virus I found like 30 more malware including Trojan ad loader and rather sophisticated rootkit. It can't be a coincidence, right?

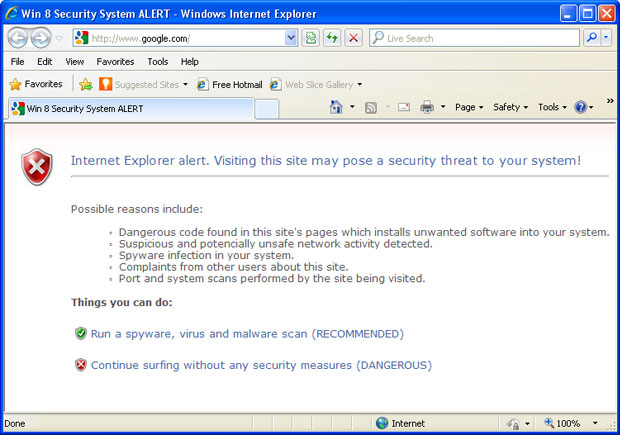
There are many variations on browser hijacking but the main idea is very simple: you are being redirected to malicous or spammy websites after conducting a search. Sometimes, click.get-amazing-results.com redirects victims to unexpected websites, you know, it works like a tracking sites. However, sometimes, it simply displays paid and very irrelevant search results or even ads which have nothing to do with your search term. All in all, click.get-amazing-results.com is a pretty direct hijack. And it's annoying as hell.
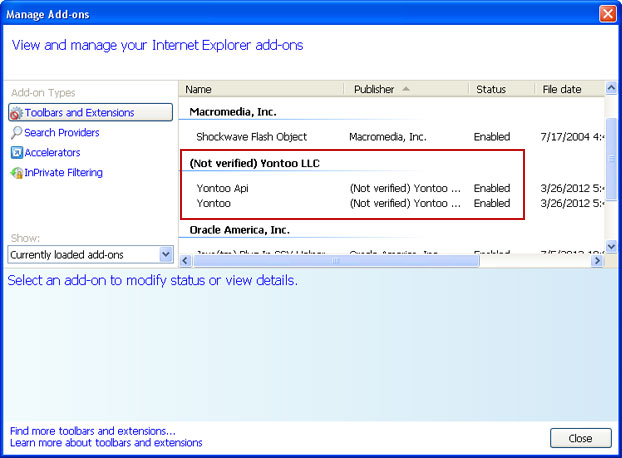
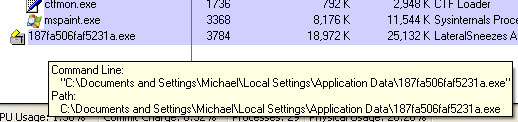
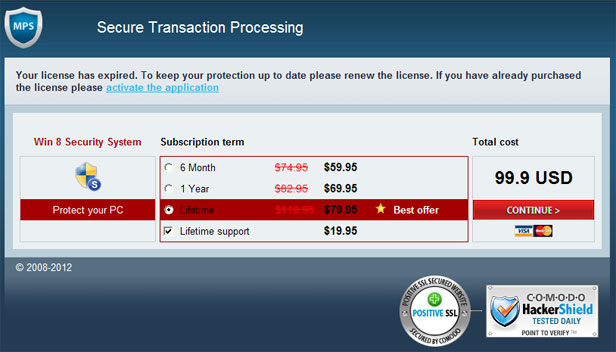
Trojan download which is responsible for get-amazing-results.com redirects usually modifies the way your system locates servers on the internet. In case of a DNS hijack a different IP address is returned. However, some malware rather than modifying your DNS settings takes a more direct route and injects malicious code into already running processes. Such malware very often infects web browser components and adds malicious browser extensions.
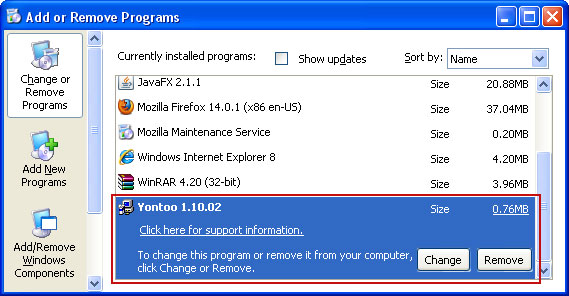
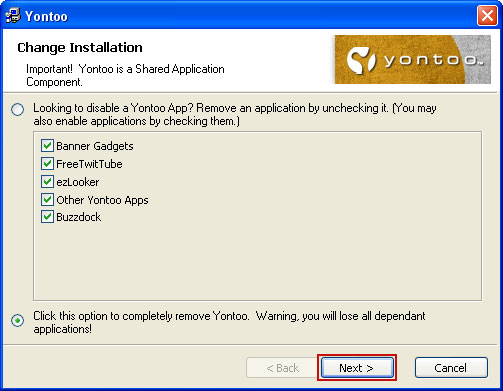
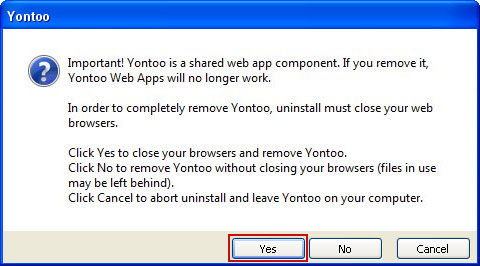
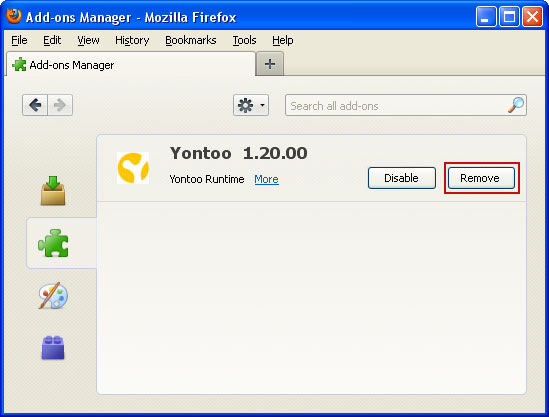
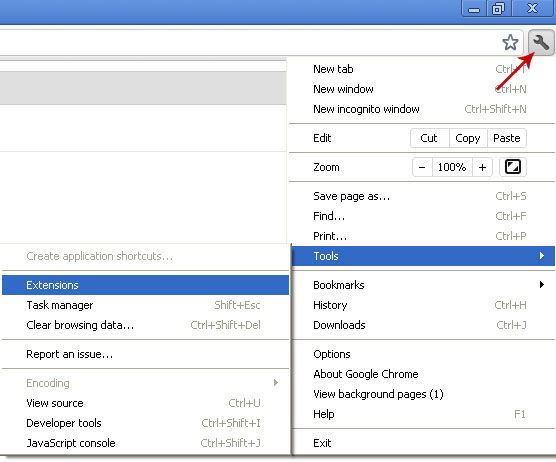
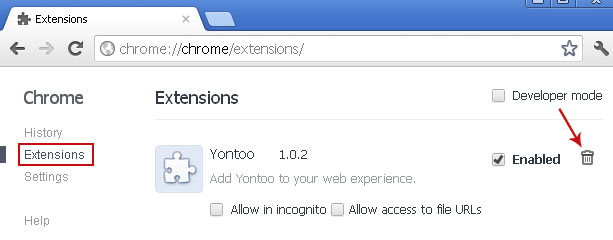
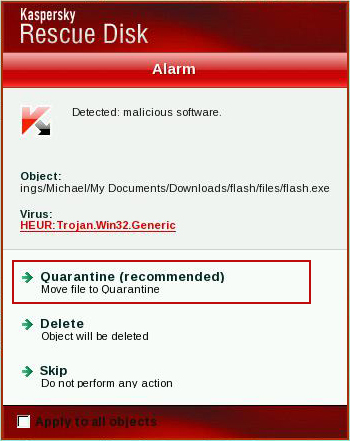
Fixing click.get-amazing-results.com redirect should be fairly easy. Run an up-to-date anti-malware scan. Please note that the website itself isn't malicious. You probably found some other sites claiming that click.get-amazing-results.com is 'malicious' or 'dangerous'. It’s only being used to redirect victims or display paid search results. It's not about the website; it's about your computer being infected with a combination of Trojan horse and probably rootkit. To remove this browser hijacker and malware associated to it, please follow the removal instructions below. Good luck and be safe online!
Click.get-amazing-results.com redirect virus removal instructions:
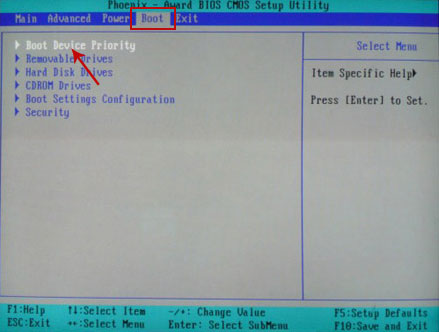
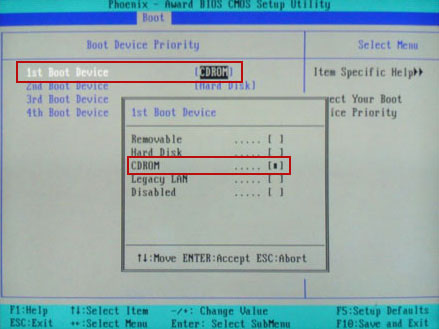
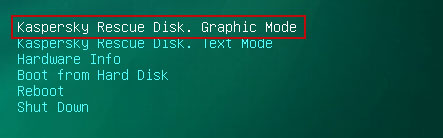
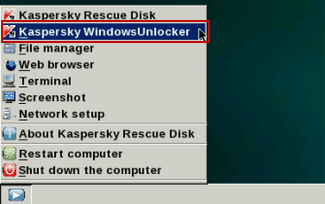
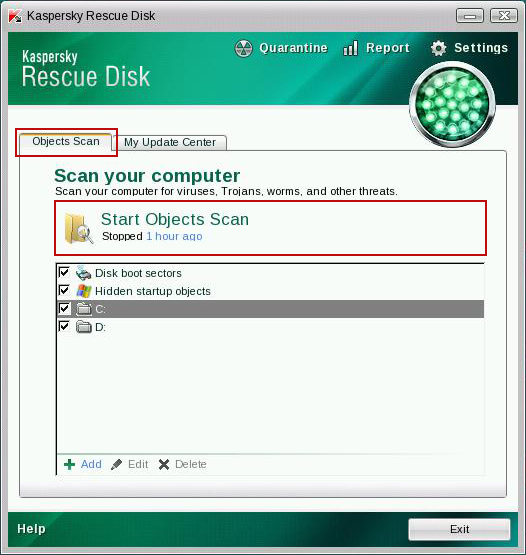
1. Download recommended anti-malware software (Spyware Doctor) and run a full system scan to remove this virus from your computer.
NOTE: in some cases malware may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe or winlogon.exe. Don't forget to update the installed program before scanning.
2. Check Windows HOSTS file.
Go to: C:\WINDOWS\system32\drivers\etc.
Double-click "hosts" file to open it. Choose to open with Notepad.
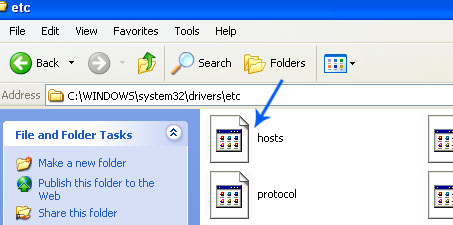
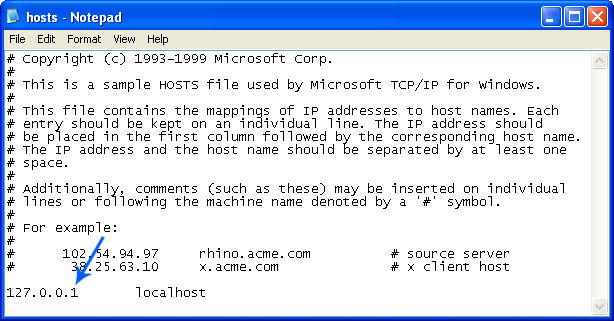
The "hosts" file should look the same as in the image below. There should be only one line: 127.0.0.1 localhost in Windows XP and 127.0.0.1 localhost ::1 in Windows Vista/7. If there are more, then remove them and save changes. Read more about Windows Hosts file here: http://support.microsoft.com/kb/972034
3. If the problem persists, please read this web document and follow the steps carefully: http://spywareremovalx.blogspot.com/2010/02/remove-google-redirect-virus.html
Tell your friends:

There are many variations on browser hijacking but the main idea is very simple: you are being redirected to malicous or spammy websites after conducting a search. Sometimes, click.get-amazing-results.com redirects victims to unexpected websites, you know, it works like a tracking sites. However, sometimes, it simply displays paid and very irrelevant search results or even ads which have nothing to do with your search term. All in all, click.get-amazing-results.com is a pretty direct hijack. And it's annoying as hell.
Trojan download which is responsible for get-amazing-results.com redirects usually modifies the way your system locates servers on the internet. In case of a DNS hijack a different IP address is returned. However, some malware rather than modifying your DNS settings takes a more direct route and injects malicious code into already running processes. Such malware very often infects web browser components and adds malicious browser extensions.
Fixing click.get-amazing-results.com redirect should be fairly easy. Run an up-to-date anti-malware scan. Please note that the website itself isn't malicious. You probably found some other sites claiming that click.get-amazing-results.com is 'malicious' or 'dangerous'. It’s only being used to redirect victims or display paid search results. It's not about the website; it's about your computer being infected with a combination of Trojan horse and probably rootkit. To remove this browser hijacker and malware associated to it, please follow the removal instructions below. Good luck and be safe online!
Click.get-amazing-results.com redirect virus removal instructions:
1. Download recommended anti-malware software (Spyware Doctor) and run a full system scan to remove this virus from your computer.
NOTE: in some cases malware may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe or winlogon.exe. Don't forget to update the installed program before scanning.
2. Check Windows HOSTS file.
Go to: C:\WINDOWS\system32\drivers\etc.
Double-click "hosts" file to open it. Choose to open with Notepad.

The "hosts" file should look the same as in the image below. There should be only one line: 127.0.0.1 localhost in Windows XP and 127.0.0.1 localhost ::1 in Windows Vista/7. If there are more, then remove them and save changes. Read more about Windows Hosts file here: http://support.microsoft.com/kb/972034

3. If the problem persists, please read this web document and follow the steps carefully: http://spywareremovalx.blogspot.com/2010/02/remove-google-redirect-virus.html
Tell your friends: