Don't Copy From This Blog...
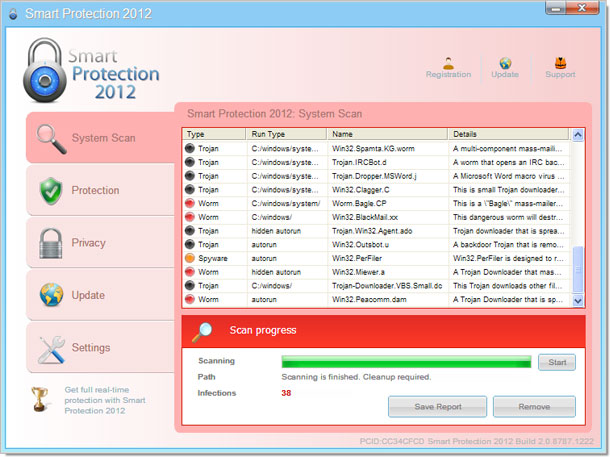
Recently we posted an article about Malicious Youtube Extensions describing how cyber crooks propagate malicious web browser extensions on Facebook and other popular social networks. This is just a quick reminder that these scams are still being spread very actively. New spam blogs are being registered every single day (probably using human-powered CAPTCHA solving services and bots). In this particular example (katesperv.blogspot.com), crooks try to lure users into installing bogus Divx Plugin which turns out to be a Premium Youtube player extension.

This isn't the most sophisticated malware attack we've ever seen because it preys on human frailties and relies heavily on user interaction. On the other hand, crooks have found a way to bypass Facebook's spam protection using Amazon web services and bit.ly URL shortener. Clicking on "Install Plugin" will load a script that checks the web browser agent and selects the correct plugins. Internet Explorer is served with online surveys.
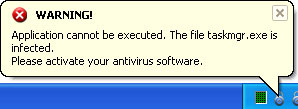
The malicious extension can access your data on all websites.

Please be very cautious when installing third-party extensions and plugins. We've said more than once: you don't need to install any other plugin or web player than Adobe Flash player in order to watch online videos. No Premium Youtube Player, Divx plugin, etc.
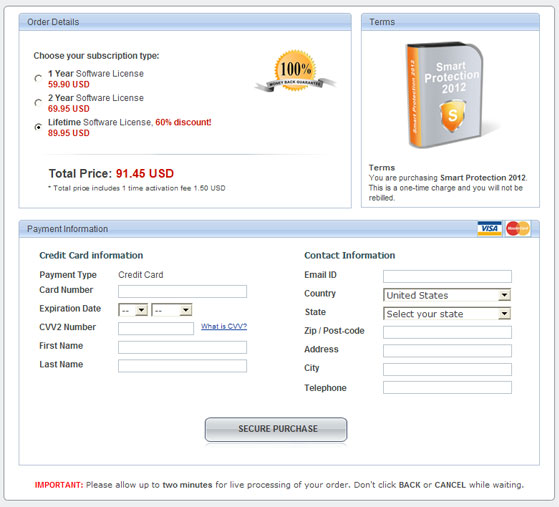
After installing malicious Youtube extension, you are taken to another web page to complete an online survey. It's the Cost Per Action (CPA) marketing model. Crooks get paid every time they get a Facebook user to complete a survey. To make sure that surveys are relevant and to increase completion rate, they use Geo IP tools to determine the geographical location of the visitor.

After all, you won't get the actual video because it doesn't even exist. At the same time, the Youtube PREMIUM Player extension will send spam messages to your friends without your permission.
The second scam advertises Free Facebook Credits (freefacebookcreditsadder.blogspot.com). Facebook Credits are a virtual currency you can use to buy virtual goods in any games or apps of the Facebook platform that accept payments. I don't really think that you can get free Facebook credits what so ever. Free Facebook Credits Adder isn't going to help you either. It leads to online survey websites as well.

Comments from unhappy customers:

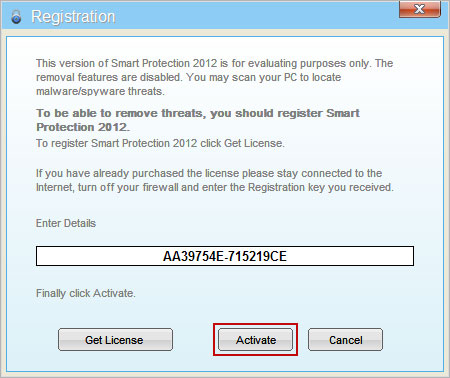
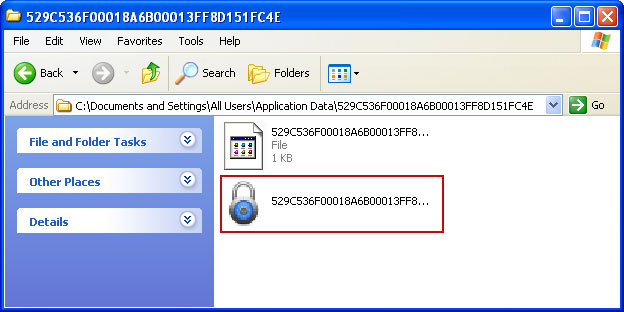
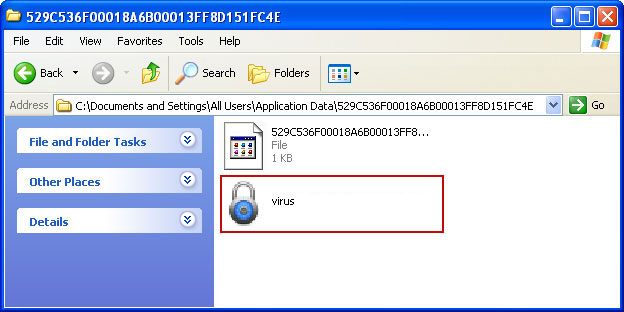
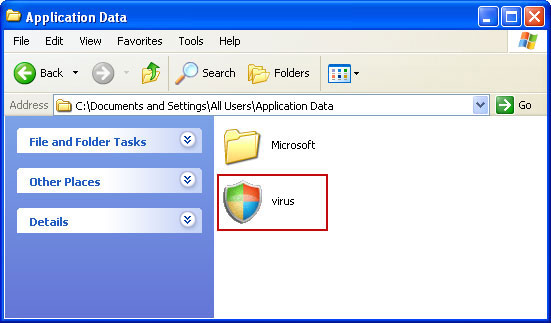
Facebook, Twitter and other social networks will play a major role in disseminating malicious programs this year, according to the latest BitDefender's malware report. Beware of Facebook scams as they are getting more and more sophisticated. If you into the Youtube PREMIUM Player, please follow this removal guide. By the way, Mac owners using Mozilla Firefox can ran into this porblem as well. Last, but not least, change your passwords. If you have any further questions, please leave a comment. Good luck and be safe online!
Tell your friends:

This isn't the most sophisticated malware attack we've ever seen because it preys on human frailties and relies heavily on user interaction. On the other hand, crooks have found a way to bypass Facebook's spam protection using Amazon web services and bit.ly URL shortener. Clicking on "Install Plugin" will load a script that checks the web browser agent and selects the correct plugins. Internet Explorer is served with online surveys.
The malicious extension can access your data on all websites.

Please be very cautious when installing third-party extensions and plugins. We've said more than once: you don't need to install any other plugin or web player than Adobe Flash player in order to watch online videos. No Premium Youtube Player, Divx plugin, etc.
After installing malicious Youtube extension, you are taken to another web page to complete an online survey. It's the Cost Per Action (CPA) marketing model. Crooks get paid every time they get a Facebook user to complete a survey. To make sure that surveys are relevant and to increase completion rate, they use Geo IP tools to determine the geographical location of the visitor.

After all, you won't get the actual video because it doesn't even exist. At the same time, the Youtube PREMIUM Player extension will send spam messages to your friends without your permission.
The second scam advertises Free Facebook Credits (freefacebookcreditsadder.blogspot.com). Facebook Credits are a virtual currency you can use to buy virtual goods in any games or apps of the Facebook platform that accept payments. I don't really think that you can get free Facebook credits what so ever. Free Facebook Credits Adder isn't going to help you either. It leads to online survey websites as well.

Comments from unhappy customers:

Facebook, Twitter and other social networks will play a major role in disseminating malicious programs this year, according to the latest BitDefender's malware report. Beware of Facebook scams as they are getting more and more sophisticated. If you into the Youtube PREMIUM Player, please follow this removal guide. By the way, Mac owners using Mozilla Firefox can ran into this porblem as well. Last, but not least, change your passwords. If you have any further questions, please leave a comment. Good luck and be safe online!
Tell your friends: