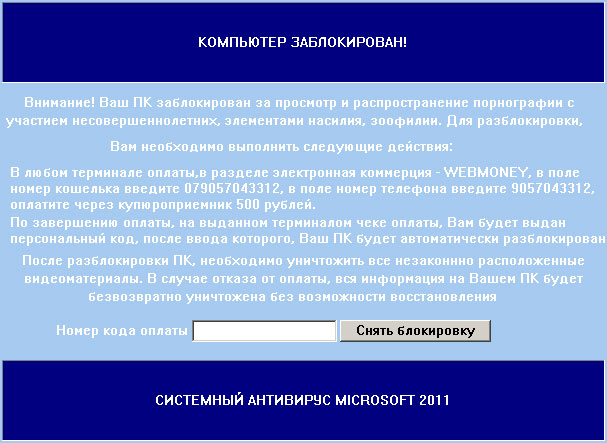
Don't Copy From This Blog...
iMesh is probably one of the oldest peer-to-peer file sharing network/software in the world. I'm sure most of you have heard about this software. Before taking a closer look at this P2P software, I think it's worth mentioning that iMesh is not a virus or any other type of malicious software that can infect your machine. However, some people find it difficult to completely remove iMesh from from their computers. Although, iMeshc can be easily uninstalled via Control Panel → Add/Remove (Uninstall), iMesh Toolbar and iMesh search bar must be removed separately. So, when you uninstall iMesh, you also have to uninstall a program called MediaBar. And that's not all, you have to restore your previous homepage and uninstall search provider(search.imesh.com) manually as well. Sounds qquite complicated. Besides, re-installing your web browser probably won't help either. And one last thing, it may add Emoticons for your messenger! icon/shortcut to your Desktop. If you don't know how to remove iMesh Toolbar and iMesh search bar, please follow the steps in the removal guide below. And if you need help removing it, please leave a comment below or just email us. Good luck and be safe online!

iMesh Toolbar and iMesh search bar removal instructions:
1. First of all, download recommended anti-malware software and run a full system scan. It will detect and remove this infection from your computer. You may then follow the manual removal instructions below to remove the leftover traces of this browser hijacker. Hopefully you won't have to do that.
2. Go to the Start Menu. Select Control Panel → Add/Remove Programs.
If you are using Windows Vista or Windows 7, select Control Panel → Uninstall a Program.
3. Search for MediaBar in the list. Select the program and click Remove button.
If you are using Windows Vista/7, click Uninstall up near the top of that window.

Remove iMesh Toolbar and iMesh search bar in Internet Explorer:
1. Open Internet Explorer. Go to Tools → Manage Add-ons.

2. Select Toolbars and Extensions. Uninstall everything related to iMesh Inc. from the list: MediaBar, UrlHelper Class, etc.

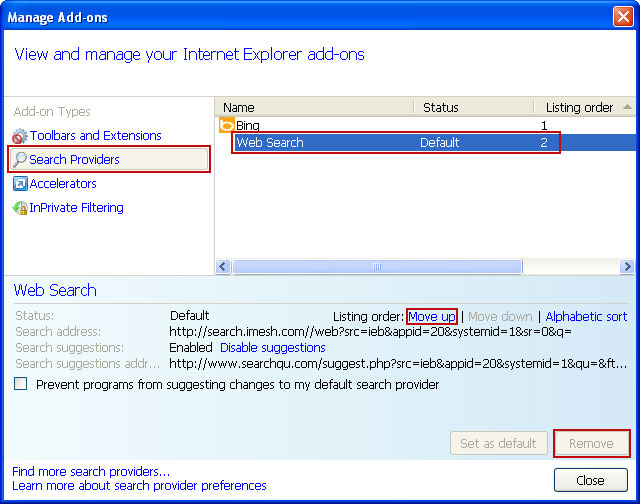
3. Select Search Providers. First of all, choose Bing search engine and make it your default search provider. Then select Web Search and click Remove button to uninstall it (lower right corner of the window).
4. Go to Tools → Internet Options. Select General tab and click Use default button or enter your own website, e.g. gooog.com instead of search.imesh.com. Click OK to save the changes. And that's it.


Remove iMesh Toolbar and iMesh search bar in Mozilla Firefox:
1. Open Mozilla Firefox. Go to Tools → Add-ons.

2. Select Extensions. Choose DataMngr and MediaBar and click Uninstall button.

3. Click the small magnifier icon at the right top corner as shown in the image below. Select Manage Search Engines... from the list.

4. Select Web Search and click Remove button. Click OK to save the changes.

5. Go to Tools → Options. Under the General tab reset the startup homepage. That's it.
Remove iMesh Toolbar and iMesh search bar in Google Chrome:
1. Click on Customize and control Google Chrome icon and select Options.

2. Change Google Chrome homepage to google.com or any other.

3. Click the Manage search engines... button.

4. Make google.com your default search engine shown in the image below.

5. Select Web Search from the list remove it by clicking the "X" mark as shown in the image below.

Associated Facemoods files and registry values:
Files:

iMesh Toolbar and iMesh search bar removal instructions:
1. First of all, download recommended anti-malware software and run a full system scan. It will detect and remove this infection from your computer. You may then follow the manual removal instructions below to remove the leftover traces of this browser hijacker. Hopefully you won't have to do that.
2. Go to the Start Menu. Select Control Panel → Add/Remove Programs.
If you are using Windows Vista or Windows 7, select Control Panel → Uninstall a Program.

3. Search for MediaBar in the list. Select the program and click Remove button.
If you are using Windows Vista/7, click Uninstall up near the top of that window.

Remove iMesh Toolbar and iMesh search bar in Internet Explorer:
1. Open Internet Explorer. Go to Tools → Manage Add-ons.

2. Select Toolbars and Extensions. Uninstall everything related to iMesh Inc. from the list: MediaBar, UrlHelper Class, etc.

3. Select Search Providers. First of all, choose Bing search engine and make it your default search provider. Then select Web Search and click Remove button to uninstall it (lower right corner of the window).

4. Go to Tools → Internet Options. Select General tab and click Use default button or enter your own website, e.g. gooog.com instead of search.imesh.com. Click OK to save the changes. And that's it.


Remove iMesh Toolbar and iMesh search bar in Mozilla Firefox:
1. Open Mozilla Firefox. Go to Tools → Add-ons.

2. Select Extensions. Choose DataMngr and MediaBar and click Uninstall button.

3. Click the small magnifier icon at the right top corner as shown in the image below. Select Manage Search Engines... from the list.

4. Select Web Search and click Remove button. Click OK to save the changes.

5. Go to Tools → Options. Under the General tab reset the startup homepage. That's it.
Remove iMesh Toolbar and iMesh search bar in Google Chrome:
1. Click on Customize and control Google Chrome icon and select Options.

2. Change Google Chrome homepage to google.com or any other.

3. Click the Manage search engines... button.

4. Make google.com your default search engine shown in the image below.

5. Select Web Search from the list remove it by clicking the "X" mark as shown in the image below.

Associated Facemoods files and registry values:
Files:
- C:\Program Files\iMesh Applications\MediaBar\
- C:\Program Files\iMesh Applications\MediaBar\uninstall.exe
- C:\Program Files\iMesh Applications\MediaBar\Datamngr\datamngr.dll
- C:\Program Files\iMesh Applications\MediaBar\Datamngr\datamngrUI.exe
- C:\Program Files\iMesh Applications\MediaBar\Datamngr\IEBHO.dll
- C:\Program Files\iMesh Applications\MediaBar\Datamngr\FirefoxExtension\chrome.manifest
- C:\Program Files\iMesh Applications\MediaBar\Datamngr\FirefoxExtension\chrome.manifest.alt
- C:\Program Files\iMesh Applications\MediaBar\Datamngr\FirefoxExtension\install.rdf
- C:\Program Files\iMesh Applications\MediaBar\Datamngr\FirefoxExtension\install.rdf.alt
- C:\Program Files\iMesh Applications\MediaBar\Datamngr\FirefoxExtension\components\DataMngrHlp.dll
- C:\Program Files\iMesh Applications\MediaBar\Datamngr\FirefoxExtension\components\DataMngrHlp.xpt
- C:\Program Files\iMesh Applications\MediaBar\Datamngr\FirefoxExtension\components\DataMngrHlpFF3.dll
- C:\Program Files\iMesh Applications\MediaBar\Datamngr\FirefoxExtension\content\DnsBHO.js
- C:\Program Files\iMesh Applications\MediaBar\Datamngr\FirefoxExtension\content\Error404BHO.js
- C:\Program Files\iMesh Applications\MediaBar\Datamngr\FirefoxExtension\content\NewTabBHO.js
- C:\Program Files\iMesh Applications\MediaBar\Datamngr\FirefoxExtension\content\overlay.js
- C:\Program Files\iMesh Applications\MediaBar\Datamngr\FirefoxExtension\content\overlay.xul
- C:\Program Files\iMesh Applications\MediaBar\Datamngr\FirefoxExtension\content\RelatedSearch.js
- C:\Program Files\iMesh Applications\MediaBar\Datamngr\FirefoxExtension\content\SearchBHO.js
- C:\Program Files\iMesh Applications\MediaBar\Datamngr\FirefoxExtension\content\SettingManager.js
- C:\Program Files\iMesh Applications\MediaBar\Datamngr\FirefoxExtension\content\Settings.xml
- C:\Program Files\iMesh Applications\MediaBar\Datamngr\FirefoxExtension\content\Settings.xml.alt
- C:\Program Files\iMesh Applications\MediaBar\Datamngr\ToolBar\chrome
- C:\Program Files\iMesh Applications\MediaBar\Datamngr\ToolBar\as_guid.dat
- C:\Program Files\iMesh Applications\MediaBar\Datamngr\ToolBar\dtUser.exe
- C:\Program Files\iMesh Applications\MediaBar\Datamngr\ToolBar\imeshbandmltbpi.dll
- C:\Program Files\iMesh Applications\MediaBar\Datamngr\ToolBar\imeshdtxmltbpi.dll
- C:\Program Files\iMesh Applications\MediaBar\Datamngr\ToolBar\manifest.xml
- C:\Program Files\iMesh Applications\MediaBar\Datamngr\ToolBar\uninstall.exe
- C:\Program Files\iMesh Applications\MediaBar\Datamngr\ToolBar\components\windowmediator.js
- HKEY_CURRENT_USER\Software\DataMngr
- HKEY_CURRENT_USER\Software\mediabarim
- HKEY_LOCAL_MACHINE\SOFTWARE\DataMngr
- HKEY_LOCAL_MACHINE\SOFTWARE\iMeshMediabarTb
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Toolbar
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Management\ARPCache\iMesh 1 MediaBar
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run "DATAMNGR"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\iMesh 1 MediaBar