Don't Copy From This Blog...
In the last few weeks we've heard numerous cases of people getting User Account Control (UAC) notifications asking them to allow msiexec.exe tu run. When we got the first e-mail, we thought that the user is experiencing system error but after quite a bit of research we found out that it was a Trojan horse masquerading as msiexec.exe. The Trojan was located in Users directory: C:\Users\[UserName]\msiexec.exe.

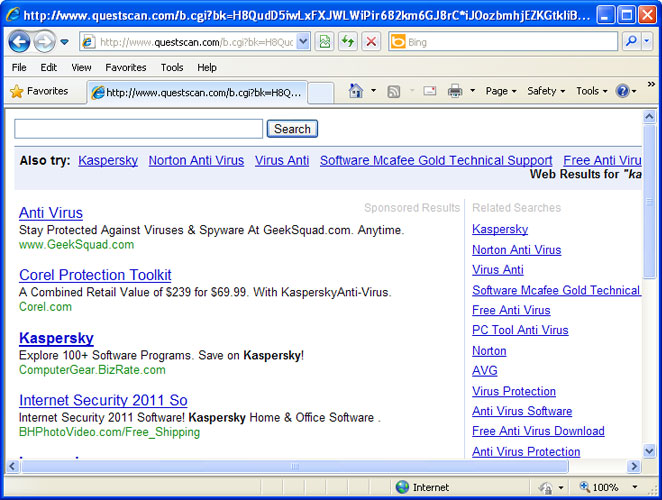
The legitimate msiexec.exe program that interprets packages and installs products is located in C:\Windows\System32 folder. But the problem is that cyber criminals try to avoid antivirus detections and confuse users by giving a malicious program the same name of some other legit programs. And when you do a Google search on the word 'msiexec.exe', you're presented with a list of results saying that it's a legitimate Windows program. In this case, the file location of the malicious msiexec.exe program (C:\Users\[UserName]\msiexec.exe) clearly indicates that it pretends to be something it's not. You can upload suspicious files to VirusTotal or Jotti to see if your suspicions were correct.
The malicious msiexec.exe downloads additional malware onto your computer. Even if you delete it manually, it may reappear after you reboot your computer. That's why we strongly recommend you to scan your computer with anti-malware software.
Download recommended anti-malware software (Spyware Doctor) and run a full system scan to remove this virus from your computer.
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe or winlogon.exe With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
Important! Do not delete the legitimate msiexec.exe located in C:\Windows\System32 folder.
If you need help removing the msiexec.exe Trojan horse, please a comment below. Good luck and be safe online!
Associated Msiexec.exe files and registry values:
Files:
C:\Documents and Settings\[UserName]\Local Settings\Temp (in Windows 2000/XP)
C:\Users\[UserName]\AppData\Local\Temp (in Windows Vista & Windows 7)
User Account Control
Do you want to allow the following program from an
unknown publisher to make changes to this computer?
Program name: msiexec.exe
Publisher: Unknown
File origin: Hard drive on this computer

The legitimate msiexec.exe program that interprets packages and installs products is located in C:\Windows\System32 folder. But the problem is that cyber criminals try to avoid antivirus detections and confuse users by giving a malicious program the same name of some other legit programs. And when you do a Google search on the word 'msiexec.exe', you're presented with a list of results saying that it's a legitimate Windows program. In this case, the file location of the malicious msiexec.exe program (C:\Users\[UserName]\msiexec.exe) clearly indicates that it pretends to be something it's not. You can upload suspicious files to VirusTotal or Jotti to see if your suspicions were correct.
The malicious msiexec.exe downloads additional malware onto your computer. Even if you delete it manually, it may reappear after you reboot your computer. That's why we strongly recommend you to scan your computer with anti-malware software.
Download recommended anti-malware software (Spyware Doctor) and run a full system scan to remove this virus from your computer.
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe or winlogon.exe With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
Important! Do not delete the legitimate msiexec.exe located in C:\Windows\System32 folder.
If you need help removing the msiexec.exe Trojan horse, please a comment below. Good luck and be safe online!
Associated Msiexec.exe files and registry values:
Files:
- C:\Windows\System32\strmdll32.dll
- C:\Windows\System32\mycomput32.exe
- C:\Windows\System32\SYSTEM32\55274-640-2001945-237251270C.manifest
- C:\Windows\System32\SYSTEM32\55274-640-2001945-237251270S.manifest
- C:\Windows\System32WINDIR%\SYSTEM32\avicap3232.dll
- C:\Windows\System32\SYSTEM32\55274-640-2001945-237251270P.manifest
- C:\Windows\System32\SYSTEM32\248321536
- C:\Windows\System32\SYSTEM32\msorcl3232.exe
- %Temp%\WER11.tmp
- %Temp%\2BA98D.dmp
C:\Documents and Settings\[UserName]\Local Settings\Temp (in Windows 2000/XP)
C:\Users\[UserName]\AppData\Local\Temp (in Windows Vista & Windows 7)
- HKEY_CURRENT_USER\SOFTWARE\
- HKEY_CURRENT_USER\SOFTWARE\IVEDHGVTFU\
- HKEY_CURRENT_USER\SOFTWARE\IVEDHGVTFU\CLSID\
- HKEY_LOCAL_MACHINE\SOFTWARE\CLASSES\.FSHARPROJ\
- HKEY_LOCAL_MACHINE\SOFTWARE\CLASSES\.FSHARPROJ\PERSISTENTHANDLER\
- HKEY_LOCAL_MACHINE\SOFTWARE\CLASSES\CLSID\{167D8C11-D0F7-4D4A-94FF-1B727D3CFC51}\
- HKEY_LOCAL_MACHINE\SOFTWARE\CLASSES\CLSID\{167D8C11-D0F7-4D4A-94FF-1B727D3CFC51}\INPROCSERVER32\
- HKEY_LOCAL_MACHINE\SOFTWARE\CLASSES\CLSID\{53FBF74C-ACD3-8E42-3397-A342CEE0B972}\
- HKEY_LOCAL_MACHINE\SOFTWARE\CLASSES\CLSID\{53FBF74C-ACD3-8E42-3397-A342CEE0B972}\INPROCSERVER32\
- HKEY_LOCAL_MACHINE\SOFTWARE\CLASSES\CLSID\{CA80A1DF-1993-458D-B1C5-8893EC9E5770}\
- HKEY_LOCAL_MACHINE\SOFTWARE\CLASSES\IVEDHGVTFU\
- HKEY_LOCAL_MACHINE\SOFTWARE\CLASSES\IVEDHGVTFU\CLSID\
- HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\BROWSER HELPER OBJECTS\{167D8C11-D0F7-4D4A-94FF-1B727D3CFC51}\
- HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\BROWSER HELPER OBJECTS\{53FBF74C-ACD3-8E42-3397-A342CEE0B972}\
- HKEY_USERS\.DEFAULT\SOFTWARE\IVEDHGVTFU\
- HKEY_USERS\.DEFAULT\SOFTWARE\IVEDHGVTFU\CLSID\