Don't Copy From This Blog...
Dr. Guard is a fake antivirus program. It reports false system security threats to scare you into thinking that your computer is infected with various malicious software. It also displays fake warnings to make you think that your computer is under attack from a remote computer and that your personal information, passwords can be stolen. Furthermore, it will even create porn icons on your desktop. How rude! Finally, as a typical rogue program it will ask you to pay for a full version of the program to remove the infections and to ensure full system protection against new threats. Sounds great, but unfortunately this is nothing more but a scam. Please don't purchase it! Otherwise you will simply lose your money. Instead, follow the Dr. Guard removal instructions below and remove this virus from your computer ass soon as possible.

Dr Guard is a clone of Paladin Antivirus. This one is also a rogue security application. Both programs look the same (use the same graphical user interface). Most of the time, DrGuard is promoted and installed through the use of trojan viruses and other malicious software. However, please note that it can come bundled with other malware too, mostly with widely spread TDSS rootkit. The bad news is that if you got Dr. Guard with this rootkit then MalwareBytes' Anti-malware won't help you, because it can't remove that rootkit at the moment. On the other hand there is a free tool for TDSS removal from Kaspersky lab. More details on this can be found in the removal guide below.
Once running, Dr. Guard performs fake system scan and displays a list of infections that can't be removed unless you buy the program. The rogue program attempts to uninstall legitimate anti-virus software if it founds one on the compromised computer. It tries to uninstall MalwareBytes anti-malware, NOD32 Antivirus, AVG, Avast!, Avira and other better known security programs. This is kind of self-protection method. What is more, it may block security related websites too. And finally, Dr. Guard displays a bunch of fake security alerts and notification from Task Manager. It even impersonates Windows Security Center and suggests you to buy the rogue program. You should ignore them just like the false scan results. You can see some of the fake Dr Guard alerts in the images below.



There shouldn't be any doubts. Dr. Guard is absolutely needless and even dangerous program. Please remove from your computer upon detection. Full details on how to remove Dr. Guard from your computer for free cab be found below. Also note, if you already purchased this fake program then you should contact your credit card company as soon as possible and dispute the charges. If you have any questions don't hesitate and leave a comment. Good luck!
Dr. Guard removal instructions:
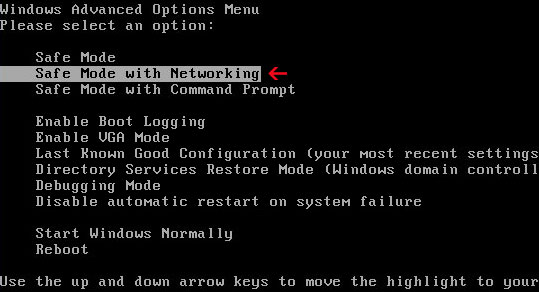
1. Download the file TDSSKiller.zip and extract it into a folder
2. Execute the file TDSSKiller.exe (NOTE: you may have to rename TDSSKiller.exe to explorer.com yourself or download already renamed explorer.com file in order to run it)
3. Follow the prompts and wait for the scan and disinfection process to be over. Close all programs and press “Y” key to restart your computer.
More detail TDSSKiller tutorial: http://support.kaspersky.com/viruses/solutions?qid=208280684
4. Download one of the following anti-malware software and run a full system scan:
5. New threats appear every day. In order to protect your PC from such (new) infections we strongly recommend you to use ESET Smart Security.
Dr. Guard associated files and registry values:
Files:
Please share this information with other people:

Dr Guard is a clone of Paladin Antivirus. This one is also a rogue security application. Both programs look the same (use the same graphical user interface). Most of the time, DrGuard is promoted and installed through the use of trojan viruses and other malicious software. However, please note that it can come bundled with other malware too, mostly with widely spread TDSS rootkit. The bad news is that if you got Dr. Guard with this rootkit then MalwareBytes' Anti-malware won't help you, because it can't remove that rootkit at the moment. On the other hand there is a free tool for TDSS removal from Kaspersky lab. More details on this can be found in the removal guide below.
Once running, Dr. Guard performs fake system scan and displays a list of infections that can't be removed unless you buy the program. The rogue program attempts to uninstall legitimate anti-virus software if it founds one on the compromised computer. It tries to uninstall MalwareBytes anti-malware, NOD32 Antivirus, AVG, Avast!, Avira and other better known security programs. This is kind of self-protection method. What is more, it may block security related websites too. And finally, Dr. Guard displays a bunch of fake security alerts and notification from Task Manager. It even impersonates Windows Security Center and suggests you to buy the rogue program. You should ignore them just like the false scan results. You can see some of the fake Dr Guard alerts in the images below.



There shouldn't be any doubts. Dr. Guard is absolutely needless and even dangerous program. Please remove from your computer upon detection. Full details on how to remove Dr. Guard from your computer for free cab be found below. Also note, if you already purchased this fake program then you should contact your credit card company as soon as possible and dispute the charges. If you have any questions don't hesitate and leave a comment. Good luck!
Dr. Guard removal instructions:
1. Download the file TDSSKiller.zip and extract it into a folder
2. Execute the file TDSSKiller.exe (NOTE: you may have to rename TDSSKiller.exe to explorer.com yourself or download already renamed explorer.com file in order to run it)
3. Follow the prompts and wait for the scan and disinfection process to be over. Close all programs and press “Y” key to restart your computer.
More detail TDSSKiller tutorial: http://support.kaspersky.com/viruses/solutions?qid=208280684
4. Download one of the following anti-malware software and run a full system scan:
5. New threats appear every day. In order to protect your PC from such (new) infections we strongly recommend you to use ESET Smart Security.
Dr. Guard associated files and registry values:
Files:
- C:\Documents and Settings\[User]\Start Menu\Programs\Dr. Guard
- C:\Program Files\Dr. Guard
- C:\Program Files\Dr. Guard\drg.db
- C:\Program Files\Dr. Guard\drgext.dll
- C:\Program Files\Dr. Guard\drghook.dll
- C:\Program Files\Dr. Guard\drguard.exe
- C:\Program Files\Dr. Guard\splash.mp3
- C:\Program Files\Dr. Guard\uninstall.exe
- C:\Program Files\Dr. Guard\virus.mp3
- %Temp%\asr64_ldm.exe
- C:\WINDOWS\system32\spoolsv.exe
- C:\WINDOWS\system32\drivers\_VOIDd.sys
- HKEY_CLASSES_ROOT\*\shellex\ContextMenuHandlers\SimpleShlExt
- HKEY_CLASSES_ROOT\CLSID\{5E2121EE-0300-11D4-8D3B-444553540000}
- HKEY_CLASSES_ROOT\Folder\shellex\ContextMenuHandlers\SimpleShlExt
- HKEY_LOCAL_MACHINE\SOFTWARE\Dr. Guard
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Dr. Guard
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableTaskMgr"
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Dr. Guard"
- HKEY_CLASSES_ROOT\CLSID\{5E2121EE-0300-11D4-8D3B-444553540000}
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Approved "{5E2121EE-0300-11D4-8D3B-444553540000}"
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableTaskMgr" = "1"
Please share this information with other people: